Unified communications platforms are constantly innovating and adapting to the rapidly changing ways we work. At the same time, financial and brand threats are growing at a record pace across the cloud—especially as hybrid and remote work continues.
That’s why businesses should always scrutinize how UCaaS vendors handle security, data privacy, and compliance. Mitigating and preventing these risks should play a key role in your buying considerations.
⭐ Want to learn more about UCaaS security? ⭐
Here’s what to look for in a UCaaS provider’s security posture.
So what should you look for when it comes to UCaaS security?
Know the security and data privacy risks
First, let’s look at some notable stats that highlight growing security risks:
- General Data Protection Regulation (GDPR): $1.25B in fines to businesses 2021
- Cost of Data Breaches: $129M in 2021, an increase of 143% over 2019
- Cost of Vishing/Smishing: $54M detected by the FBI in 2020
- Cost of Downtime Per Min: $5,600 per min estimated by Gartner IT
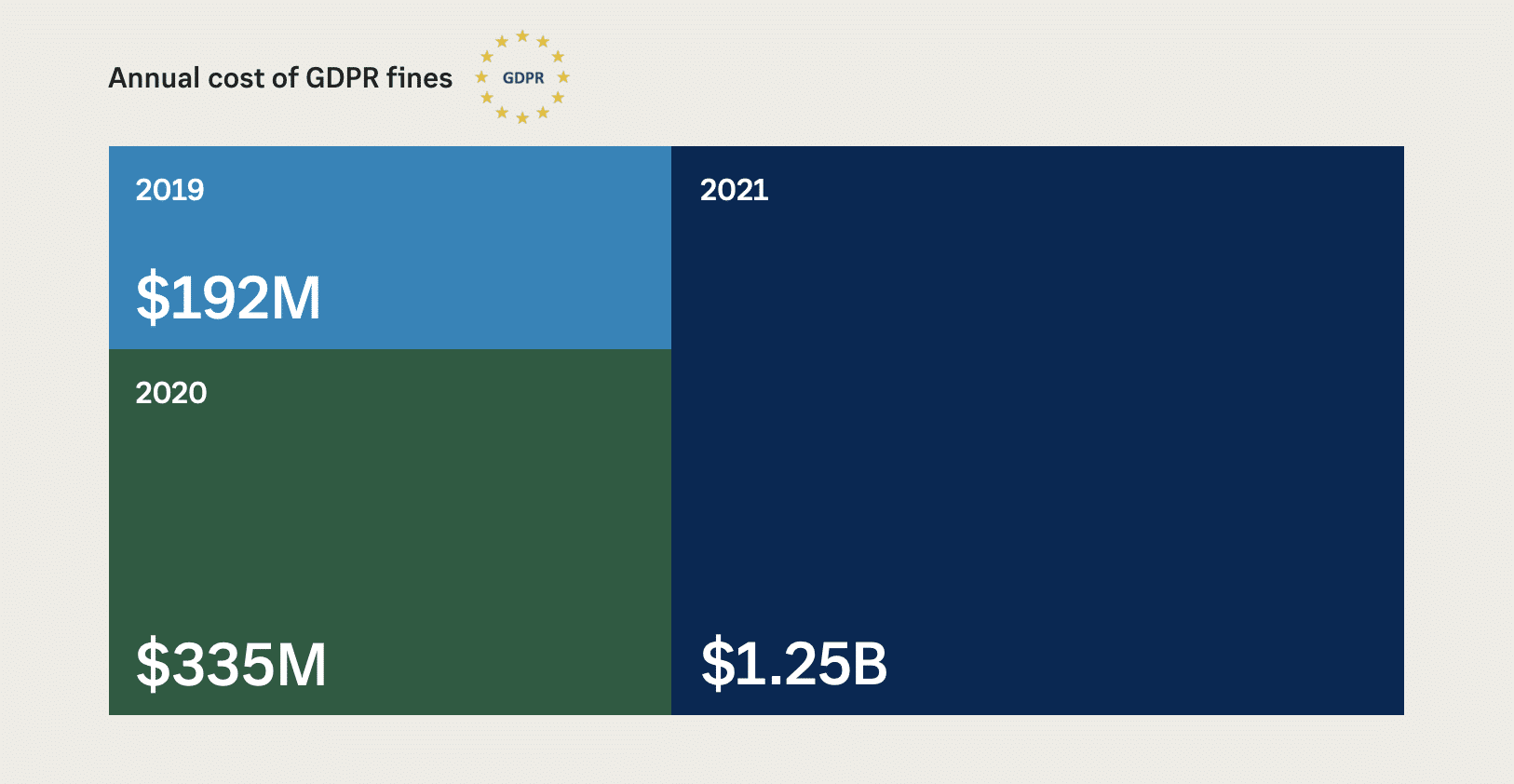
Think of it this way: Your UCaaS vendor’s security infrastructure is, in essence, an extension of your environment. Your vendor should be transparent about the investments they’ve made to safeguard your users and data from security threats and data loss—day in and day out.
If your UCaaS vendor’s security is lax, then your organization will be more vulnerable to a breach that can harm your brand value and bottom line.
With the right technical controls, a UCaaS platform can be built with security, privacy, and compliance at the center of its infrastructure investments and innovation strategy.
RingCentral: A leading approach to UCaaS trust
Security is in our DNA. With over 100 years of experience collectively, our IT security veterans take a multi-dimensional approach to the safety of your data by applying best-in-class technologies and rigorous processes.
1. Best-in-class DevSecOps
From our product design to the operations of our business, we employ rigorous security and data best practices in everything we do. We provide our customers with a robust security platform by integrating security principles into the development process from the get-go.

2. Secure-by-design platform
We tirelessly pursue a shared responsibility model where we maintain third-party certifications and attestations that validate our information security policies and practices along with customer controls—so you can directly manage your use case needs.
3. High reliability and uptime
Our security experts proactively monitor and optimize the platform 24/7/365 to ensure the availability of your service remains at the highest level possible. We stand by this commitment with an industry-leading service level agreement (SLA) of 99.999% uptime offered in over 45+ countries. And we’ve consistently met that promise for 12 consecutive quarters.
With over 15 geographically dispersed data centers and media points of presence, we provide a global infrastructure that ensures 24/7 business continuity for your company—from anywhere.
Our secure infrastructure
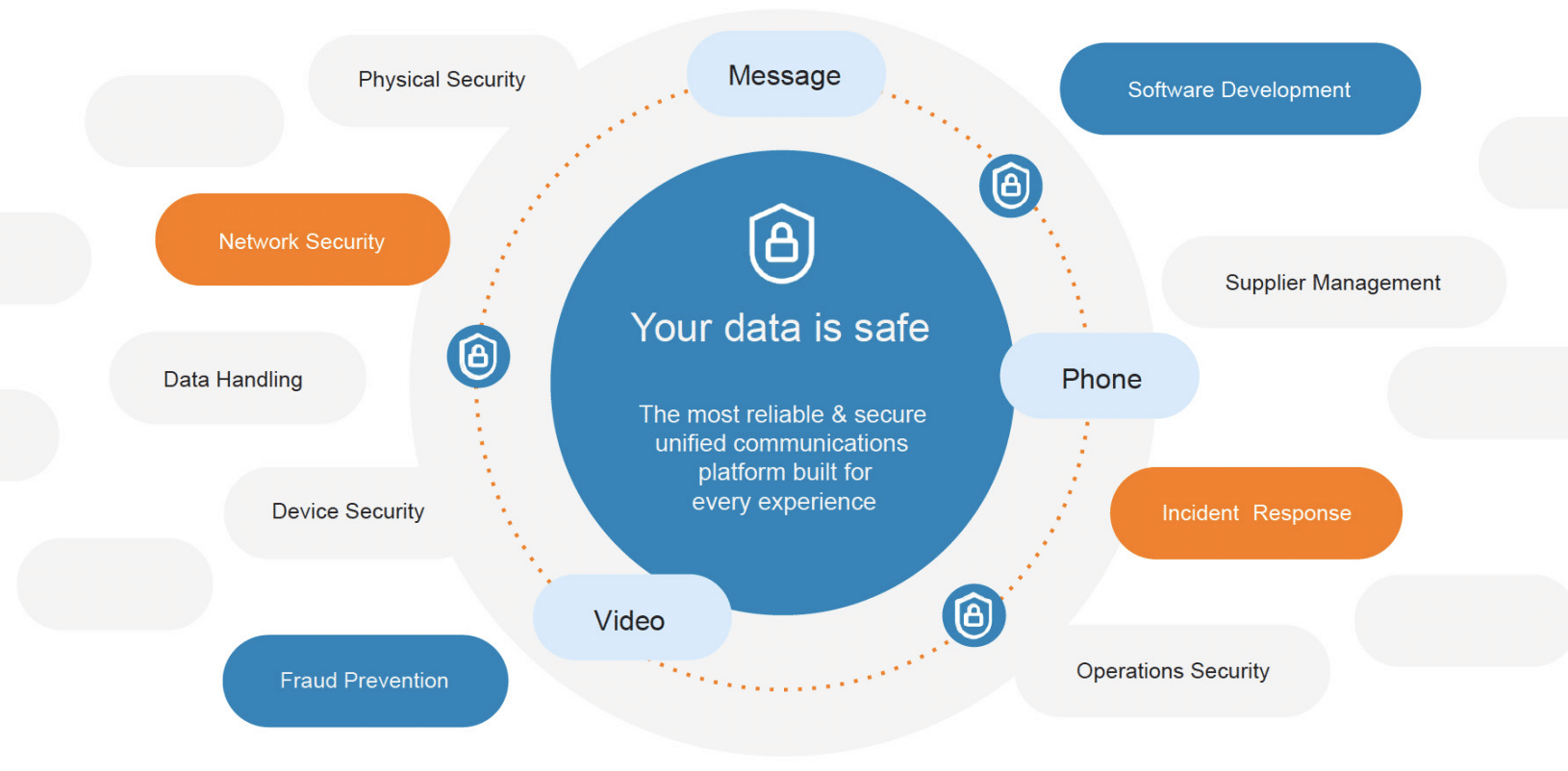
RingCentral’s security posture consists of numerous controls that reflect the best practices from established information security industry standards. Collectively, these stringent controls allow us to achieve world-class security practices for our customers.
Our global data privacy and security certifications and attestations
Our third-party attestations and certifications speak to our commitment to data security. RingCentral is built on a secure cloud platform with a robust portfolio of security and compliance certifications, including SOC 2, ISO 27001 and 27017-18, UK Cyber Essentials Plus, German C5, GDPR, and much more.

See the full list and learn more about our independent certifications here.
Security and administrative policy controls
The RingCentral platform provides our customers with leading-edge security and policy controls that ensure a safe and secure experience for your users.
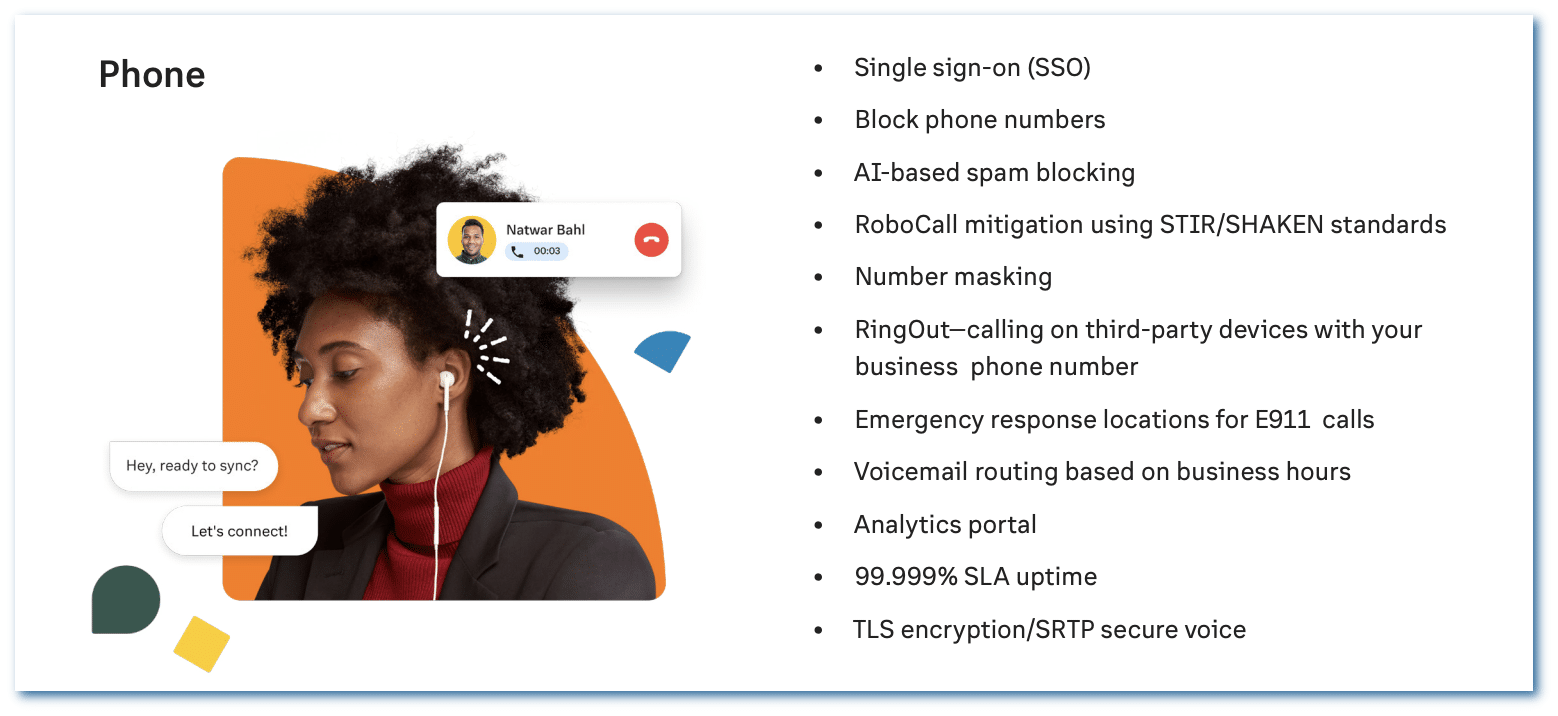
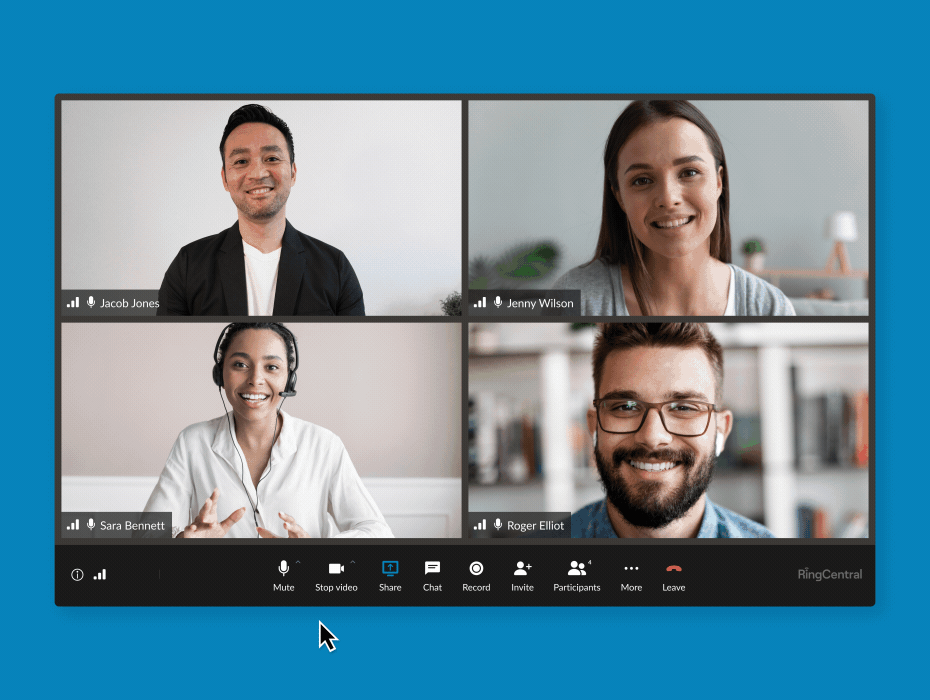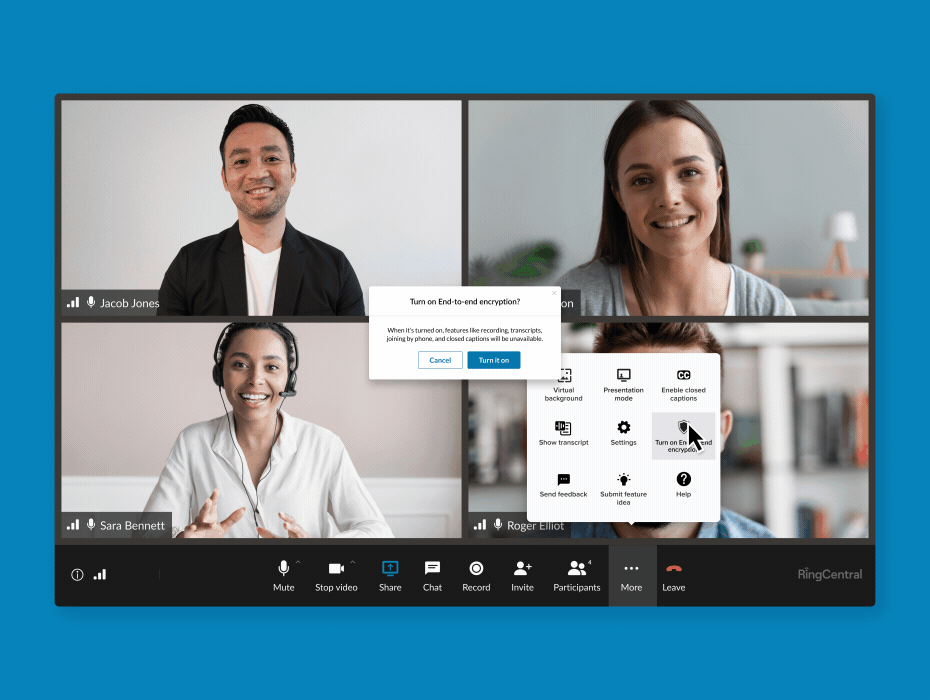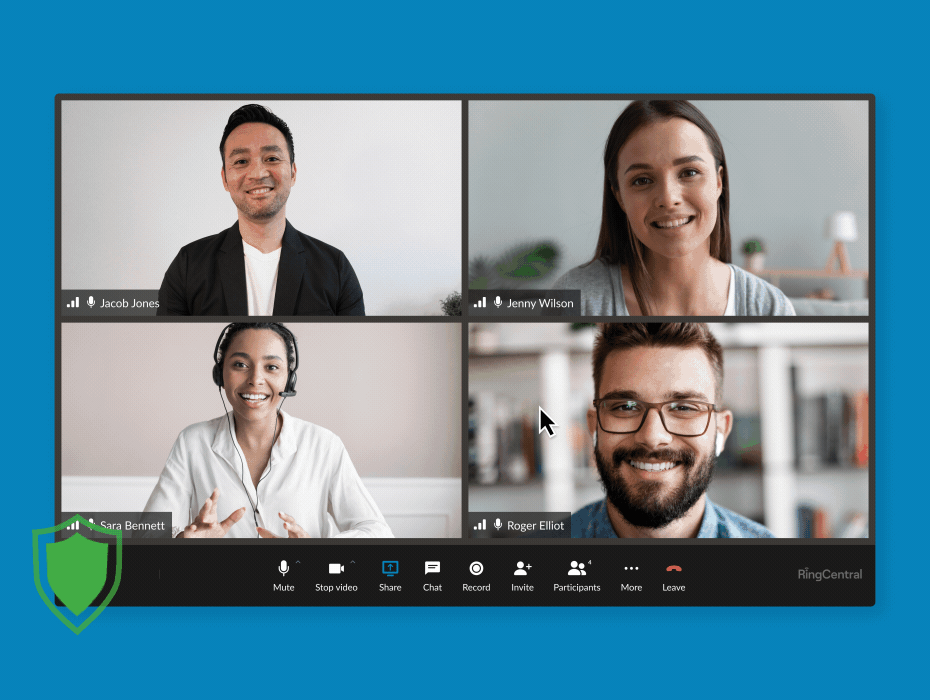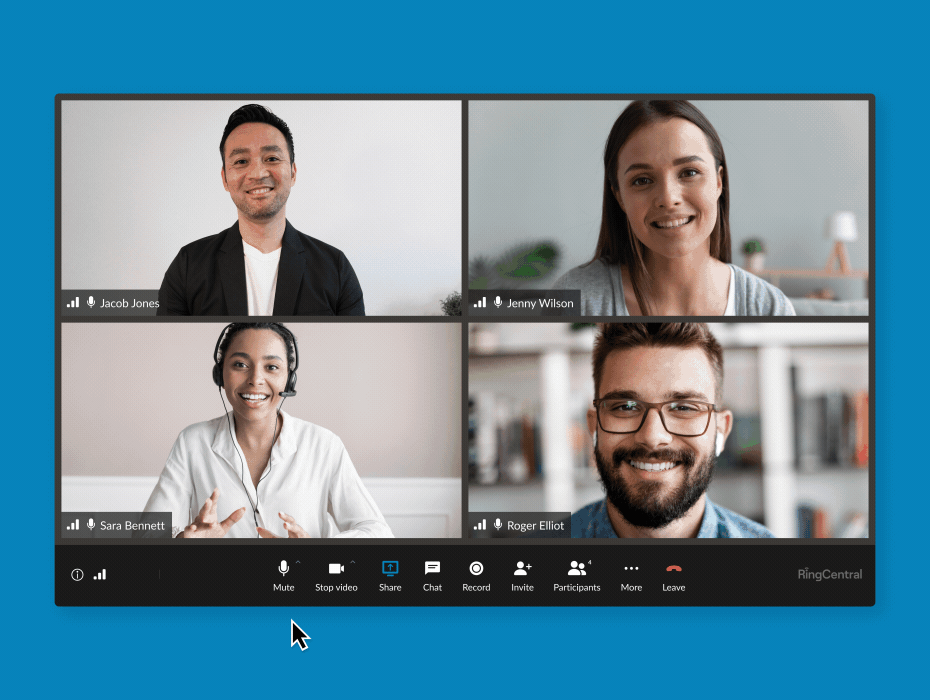
A brief snapshot of phone security controls
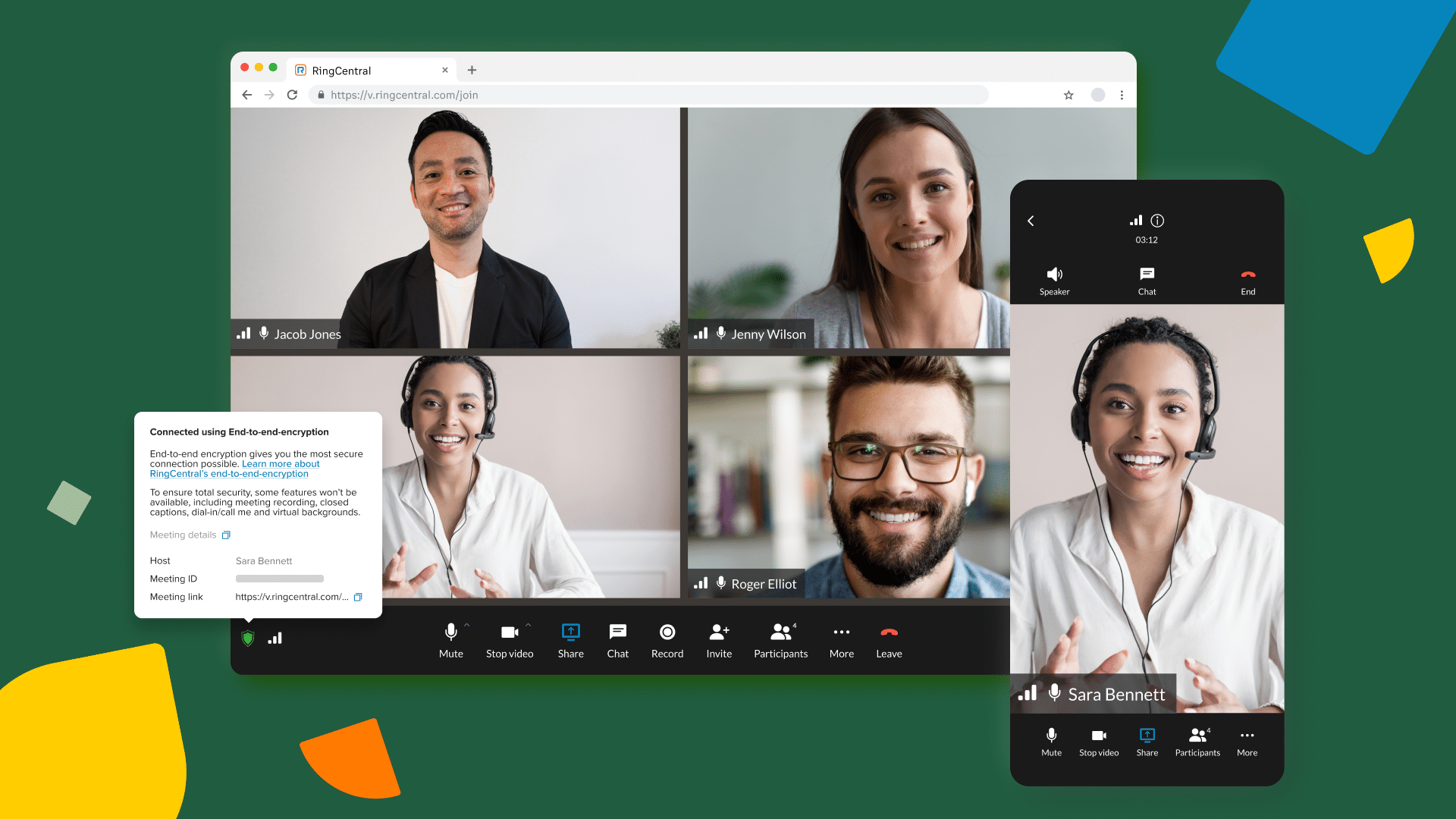
Our platform puts a comprehensive set of administrative controls across video, message, and phone at your fingertips, such as advanced call and fax blocking, requiring your meeting attendees to authenticate, limiting who can enable screen sharing, and requiring waiting rooms for your users to approve attendees who can join.
These provide you with best-in-class security capabilities to safeguard your organization from data loss and bad actors.
See the full list of security and administrative controls available for the RingCentral MVP app here.
A fundamentally different approach to global trust
RingCentral offers a fundamentally different approach to global trust for your unified communications platform. From our industry-leading five 9s in uptime reliability to our comprehensive information security protection and global privacy management, you don’t have to worry about your data being compromised or falling short of regional regulatory standards.
Our innovations and commitment to security, data privacy, and compliance have earned RingCentral recognition as a trailblazer in the market, including seven consecutive years of being named a Leader in the Gartner Magic Quadrant for Unified Communications as a Service (UCaaS).
Our approach delivers “always-on” information security protection and data privacy management that keeps your data safe and compliant with the law. And our platform provides a comprehensive toolset for your administrators and users with a breadth of dynamic and real-time controls.
Want to know more about how we protect your data? Visit the RingCentral Trust Center.
Originally published Aug 02, 2022, updated Jul 26, 2024