Highlights:
- As teams continue to work from anywhere, their communications should enable them to freely ideate and collaborate without compromising their security.
- We build security into every layer of RingCentral MVP™—from single sign-on to end-to-end encryption and data retention.
- Read more about how we protect your data in our blog: RingCentral’s stance on protecting your data.
When most of our jobs turned remote last year, cloud communications kept businesses going. Workers sent more chat messages, joined more video meetings, and made more phone calls than ever before. And the silver lining is, it worked. The massive shift to remote was a success—and it’s here to stay.
Which brings us to the future. We know that teams will increasingly work from anywhere and teams become more distributed. We also know that our communication tools should enable workers to stay connected, work together, and achieve their very best.

RingCentral’s stance on protecting your data
As more workers collaborate from anywhere, their technologies have the progressively difficult task of keeping their data protected—wherever workers are. From the messages they send to the contents of their video meetings, teams should be able to freely collaborate without compromising their security.
“The Covid-19 pandemic and the rapid move to all-remote work has changed how we work. Instead of impromptu conversations in the hallway, we are using collaboration platforms to help us update status, exchange ideas, and stay in touch.
All of these communications, and data, are, and should be, accessible only to your employees. At RingCentral, we provide secure communications to support your collaboration needs.”
At RingCentral, we understand that security is a number one priority for companies—and that’s why protecting your data is also one of our top priorities. Our products and features have the highest levels of protection baked right in, so there’s no tradeoff between great collaboration capabilities and enterprise-grade security.
Here’s a rundown of our holistic approach to the security of our flagship product RingCentral MVP:
The 4 building blocks of RingCentral MVP security
1. Identity access management
Supporting secure use of our RingCentral MVP platform starts by making sure that only authorized individuals have access.
RingCentral Single Sign-on integrates easily with any identity provider supporting SAML 2.0 (Security Assertion Markup Language 2.0), including PingFederate, Okta, or your homegrown identity provider.
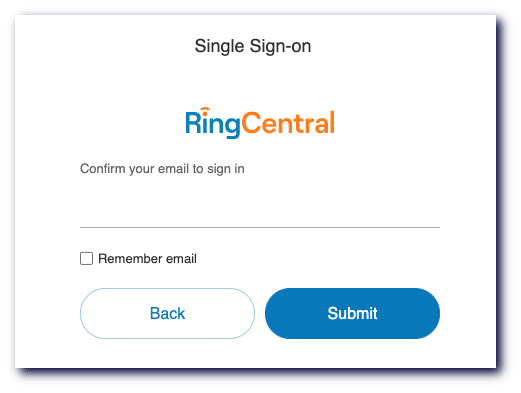
We also support Google’s SAML Implementation for Single Sign-On (SAML SSO) and Google login (OAuth 2.0). This allows you to retain control over your user’s authentication credentials and process, providing them with easy access to RingCentral and you with peace of mind.
We also make user provisioning easy. RingCentral supports Active Directory Integration, allowing users to easily log in to the RingCentral system using Okta and their current Active Directory credentials.
2. Secure meetings
Video meetings are a big part of your work—but they also present malicious parties an opportunity to access confidential information. For example, a host might accidentally expose information to a broader audience than intended, such as external guests.
We have multiple security measures built into our video meetings:
Disable recording
Sometimes you want what happens in a meeting to stay in the meeting. RingCentral’s disable recording feature allows admins to restrict meeting hosts and participants from recording the session.
Enforce password
Restrict meeting participation to authorized individuals only by requiring a password to join. Passwords can be set at the individual meeting level or can be enabled at the user or account level for all meetings and webinars.
Mute/remove participant
Meeting hosts retain full control over meeting participation and have the ability to mute or remove participants.
Waiting rooms
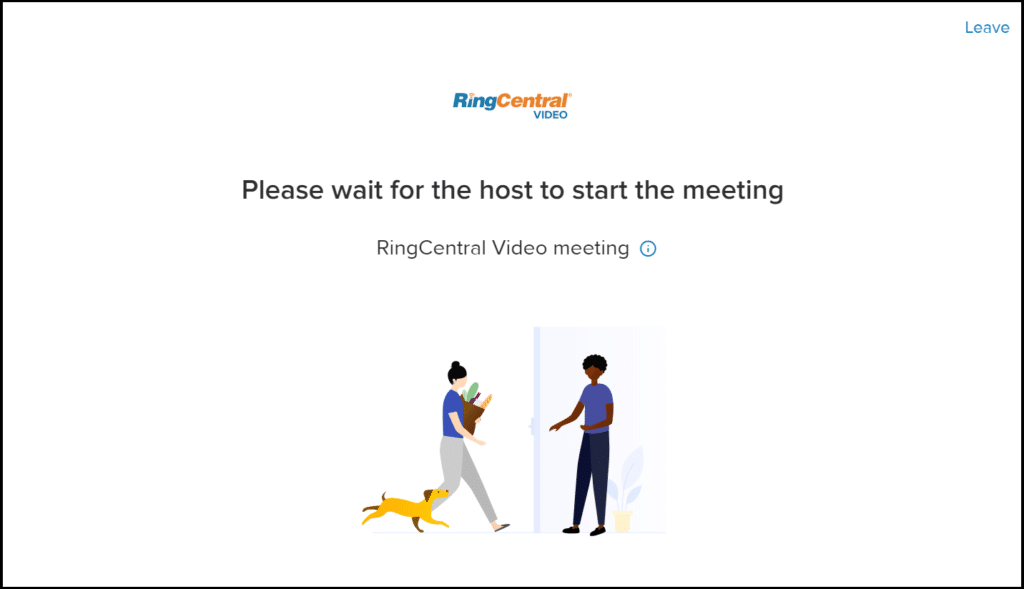
Hosts have the ability to control who enters their meetings and when. When the waiting room is enabled, participants first enter a waiting room where they hold until the host admits them.
Participants can be admitted individually, or all at the same time, and the waiting room can be enabled for all participants, external participants only, or users who are not signed in.
Disable video
Meeting hosts have the ability to restrict video usage during a meeting. This includes the ability to block or allow video enabling. If blocked, video is disabled and participants are unable to turn on their cameras. If allowed, video is disabled but individuals may choose to turn on their cameras.
Restrict screen sharing
Screen sharing during a meeting can be limited to the host or moderator only, and participants’ ability to share screens can be turned off.
Authenticated users only
Restrict meeting participation to authenticated users only, including signed-in coworkers and signed-in RingCentral users.
Lock personal rooms
Meetings in a user’s personal room can be locked once all participants have joined, preventing an authorized participant from joining using the personal room link.
Virtual backgrounds
To keep surroundings private while still allowing video participation, users can replace their background with pre-built or customizable virtual backgrounds.
3. Data protection
Cloud-based communications involves both the transfer and storage of data—and we encrypt data both when it is in transit and at rest. This means that data is converted into an unreadable form and can only be converted back with an encryption key. Data in transit is encrypted using TLS encryption and data content by AES-256 encryption.
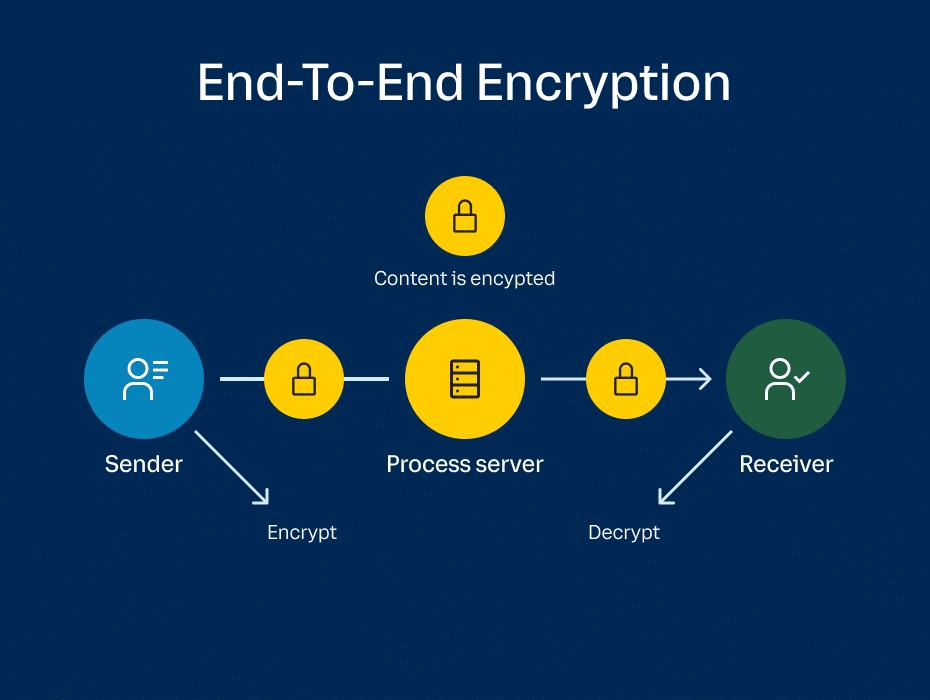
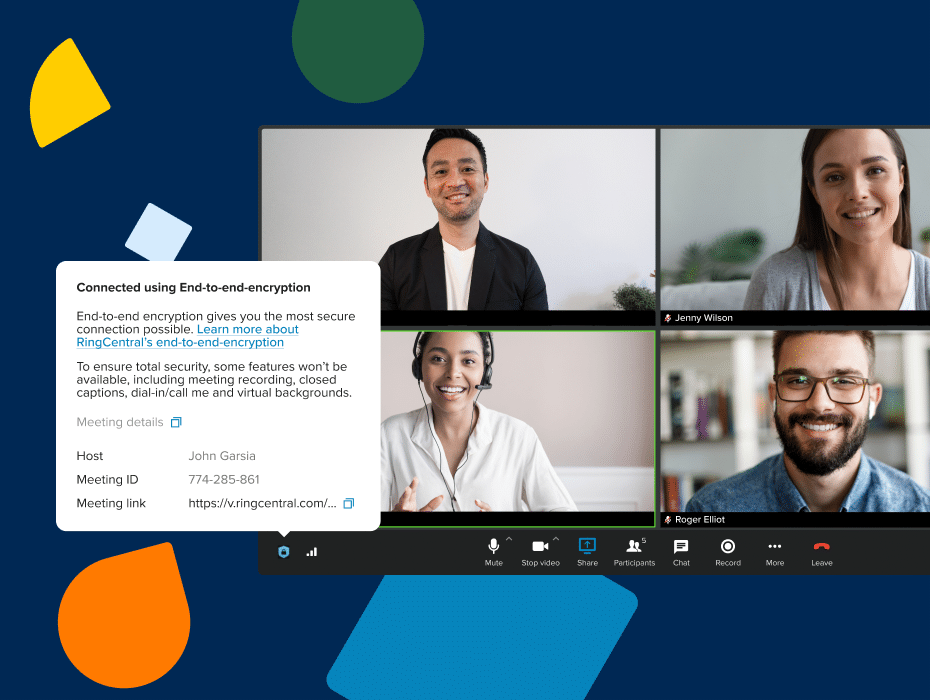
We’re also excited to announce the launch of Dynamic End-to-End Encryption (E2EE), which provides an additional layer of protection for your video meetings, such that ONLY the meeting participants can access the meeting and its contents.
With Dynamic E2EE, meeting content (voice, video) leaves users’ devices in a completely encrypted form and is only decrypted at the other participants’ devices. This means that no one is able to eavesdrop on the meeting, from non-meeting participants, to employers, to RingCentral, or anyone else in between.
The best part? Our Dynamic E2EE can be toggled on or off at any point in a meeting. This gives users the freedom to ideate and discuss “off the record” without any fear of compromising sensitive information.
Dynamic E2EE will be available on RingCentral for mobile, desktop, and web browsers. Open beta is now available, with general availability planned for October 2021.
4. Compliance and auditing
Many businesses need to comply with complex international, regional, and industry requirements that govern the collection and use of data. That’s why admins can choose how we store their RingCentral MVP data.
Data retention
Every day, your teams and workers send messages, join meetings, and make phone calls through RingCentral. At the same time, they also generate countless amounts of communications data, some of which might be important to you.
But we don’t keep that data forever. In fact, how long we store certain account data depends on the form of communication (which can be found in our data retention policy). For example, call recordings are saved for 90 days (unless specified by an admin), while outbound faxes are saved for 30 days.
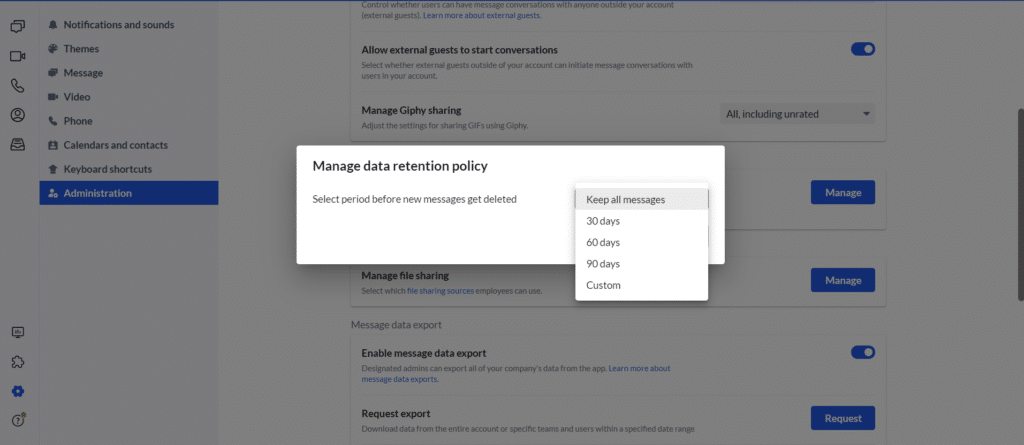
Messages are stored indefinitely by default, unless specified by the admin. Admins can choose how long their company’s team messages are stored, including forever. They can also choose to have messages deleted after a certain period of time, after which messages are wiped forever.
You can find our data retention policy here.
Archiving
Want to keep your data for longer than we store them? Developers have the ability to archive all of their RingCentral usage data, including video meeting recordings, call logs, call recordings, SMS text messages, fax, and voicemails.
There are multiple ways developers can archive their data, but we suggest using the RingCentral Archiver app. RingCentral Archiver integrates your RingCentral account with your preferred cloud storage provider such as Box, Smarsh, Dropbox, Google Drive, or an SFTP server. But most importantly, it’s built to make backing up your data simple and automatic.
Businesses in highly regulated industries can use RingCentral for Theta Lake, which helps compliance and legal teams to retain, retrieve, and review fully threaded messages and files. Messages are constantly analyzed against 40+ different compliance policies and given risk scores so you’re always on top of your security.
More instructions on exporting and archiving your data can be found here.
Protecting your teams to work from anywhere
Companies have to make some tough decisions about their return to work, but they can rest assured that their employees—and their data—are fully protected, in every part of their RingCentral experience. It’s all part of our mission to help teams stay connected—wherever they work.
Keep an eye out for upcoming security announcements, including the Dynamic End-to-End Encryption open beta, coming August 30.
In the meantime, learn more about end-to-end encryption below.

Everything you need to know about how we protect your communications data
Updated Dec 30, 2022