Highlights
- Cyberattacks have increased by 400% since the beginning of the 2020 pandemic
- Companies pursuing remote/hybrid work setups must take cybersecurity challenges seriously
- Proper training, investment, and standard operating procedures for cybersecurity can minimize risk
Remote work isn’t a new concept, but its adoption has reached a new level since the outbreak of the COVID-19 pandemic. In a short amount of time, organizations of all sizes were forced to move their employees to home offices, giving up the security of their closely-guarded enterprise networks in the process.
For 80% of employees, it was their first time working from home and dealing with the associated cybersecurity challenges, according to a June 2020 IBM Security and Morning Consult “Work From Home Survey.”
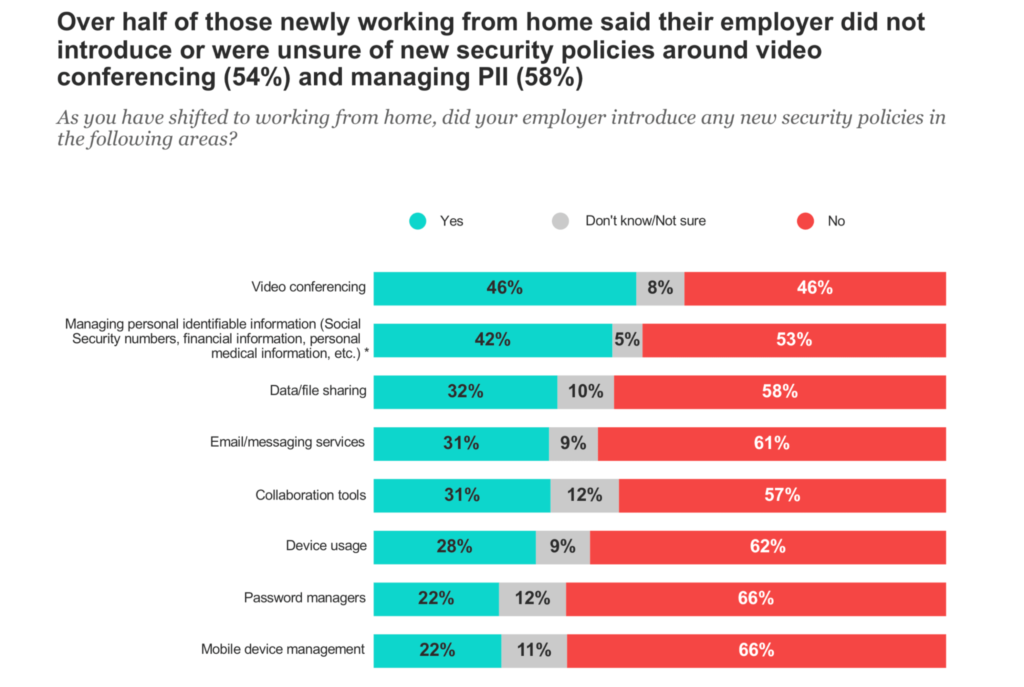
Cybercriminals didn’t waste a minute before taking advantage of the global crisis, with the FBI reporting a 400% increase in cyberattacks since the start of the pandemic. Fast forward to today, and many employees are yet to return to their offices—in fact, some never will because organizations have realized the benefits of remote work are too great to ignore.
But even though coronavirus containment measures are gradually being relaxed, the cybersecurity challenges created by the pandemic are still present. All organizations that wish to let their employees work remotely must learn how to keep their business data secure unless they’re willing to risk a costly data breach.
Understanding the security dangers of remote work
The security dangers of remote work stem from the fact that employees are not experts on cybersecurity.
That’s not an issue when working from the office and using a work computer connected to the enterprise network. But it quickly becomes a major source of risk when working from home, using a mix of personal and work devices connected to a Wi-Fi network shared by all family members.
What’s more, remote employees are far more likely to get distracted than their office-based counterparts. They may even experience the negative psychological effects of isolation and lack of work-life separation. All these factors make them more susceptible to social engineering attacks, such as phishing or spear-phishing, a more sophisticated and elaborate version of phishing that targets specific organisations or individuals.
To make matters even worse, the average home is much less physically secure than the average office building—so the theft of work devices is a real issue that must be tackled to keep important business data truly secure.
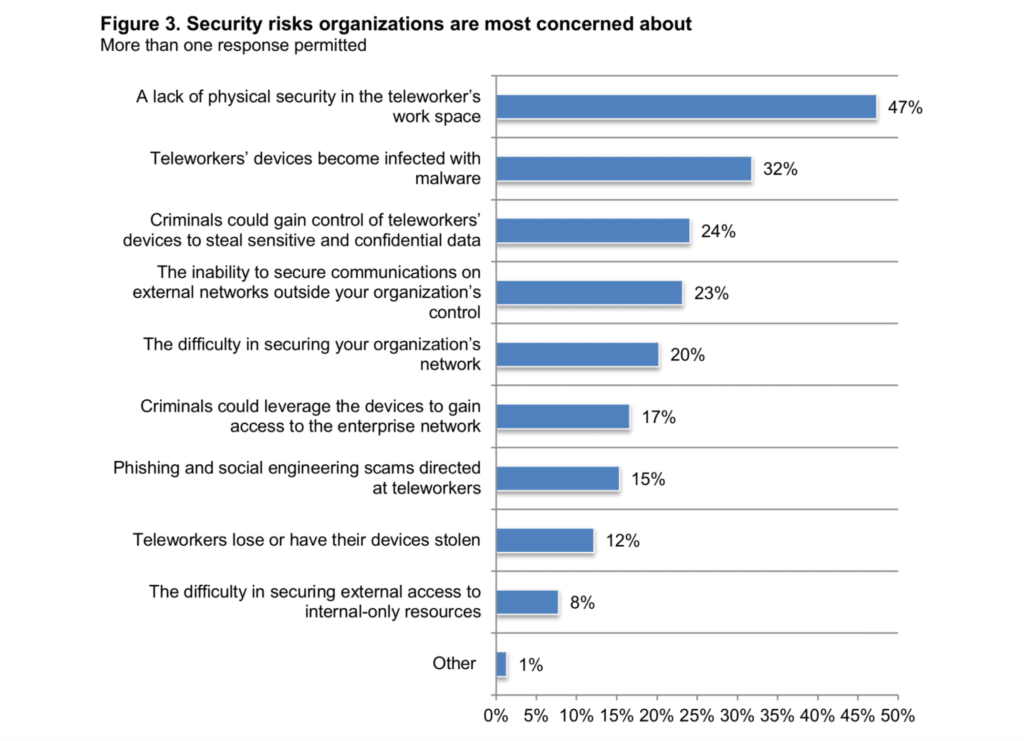
71% of organizations are very concerned about remote workers being the cause of a data breach, according to Cybersecurity in the Remote Work Era: A Global Risk Report.
The good news is that business leaders and their employees can do a lot to successfully overcome the cybersecurity challenges of remote work, and, in the next section of this article, we describe 10 effective methods that can be implemented without spending too much time or money.
How to protect business data when working remotely
To effectively protect business data when working remotely, it’s important to take into consideration that remote employees are exposed to not just digital but also physical threats.
1. Conduct cybersecurity awareness training
It’s often said that people are the weakest link in the cybersecurity chain, so re-enforcing it is often the most cost-effective way to prevent data breaches.
Your organization should carry out periodical cybersecurity awareness training to educate employees on common threats, such as:
- Social engineering attacks
- Computer sharing and personal use
- Unpatched devices
- Insecure home Wi-Fi
- Weak passwords
Cybersecurity awareness training can be done as an online course, making it possible for employees to complete it at their own pace and review learned content at any time. It’s generally recommended for employees to complete their cybersecurity training at least once a year, but more often is always better—as long as productivity remains unaffected.
For cybersecurity awareness training to deliver the best results possible, it’s a good idea to supplement it with mock cybersecurity exams. Such exams make it possible to evaluate how much employees have actually learned and whether further training is necessary.
2. Invest in endpoint security
While it’s true that trained employees are any organization’s best defense against cyber threats, even the most security-minded individuals can make a mistake and accidentally open a malicious attachment or respond to a phishing email, not realizing who its real sender is. In such situations, endpoint security can save the day.
Remote employees should have up-to-date anti-malware and firewalls installed and properly configured on all devices—not just those they use for work. Why? Because malware and other digital bugs can quickly spread to all devices connected to the same network.
Fortunately, modern operating systems already come with effective malware protection, so basic endpoint security can be achieved just by keeping it enabled and updated. Of course, you can always go a step or two further and purchase an enterprise-grade endpoint security solution from a major vendor. Just keep in mind that you could need outside help with its installation and maintenance.
3. Protect internet connections
Wi-Fi networks are wonderfully convenient, but their visibility also makes them dangerous. Unless secured properly, a cybercriminal could easily snoop on your employees’ private communications and steal sensitive information.
If nothing else, then you absolutely must ensure that your employees have secured their home Wi-Fi networks with strong passwords using either the WPA2 or, better yet, WPA3 security protocol. Contrary to what many people still believe, a strong password doesn’t have to be impossible to remember. A long passphrase consisting of several randomly selected words can get the job done even better.
Since data packets must leave the Wi-Fi network at some point to reach their end destination, remote employees must use a virtual private network (VPN) to create an encrypted tunnel through which data can securely flow over any unsecured public connection.
4. Encrypt sensitive information
Encryption is another highly effective way organizations with remote employees can protect themselves against data breaches. There are two principal types of data encryption to consider:
- At-rest: protects files where they are stored, such as on a hard drive or mobile device.
- In-transit: protects files while they’re being transferred to a different location, typically over the public internet.
At-rest encryption can be accomplished using full volume encryption software like BitLocker (Windows) or FileVault (macOS). The idea here is to make the encrypted files unreadable unless the correct password is provided. That way, a stolen hard drive full of important business documents will appear to contain nothing but random sequences of ones and zeros.
In-transit encryption relies on technologies such as HTTPS and FTPS, which are supported by most modern applications and websites. In fact, organizations have no reason whatsoever to use their plain-text counterparts because the risk is simply too great.
5. Establish a remote working policy
When the coronavirus pandemic disrupted established work routines early in 2020, many organizations were forced to abruptly transition to remote work without having enough time to set up proper policies.
If you’re among those organizations that still haven’t developed a remote work policy, then you should work on it as soon as possible to ensure that your employees know what they need to do and what’s expected of them.
Here are some key areas your remote work policy should cover:
- The use of personal devices for work-related purposes.
- When remote employees are expected to be available.
- How an employee’s productivity will be measured.
- Technical support offered to remote workers.
- Physical and digital security.
- Code of conduct during virtual meetings and other forms of communication.
For the remote working policy to actually accomplish anything meaningful, employees should be formally required to review it and confirm with their signature that they understand it. The policy should then be periodically reviewed and updated to reflect changes in technology business practices.
6. Back up all important data
Malware and hacking attempts are just two common causes of data breaches. Other reasons why important business data sometimes gets lost include:
- Human error
- Software corruption
- Hardware damage
- Device theft
- Natural disasters
Because the potential causes of data loss are so numerous, completely avoiding them all is an impossible task—at least, in the long run. Knowing that data loss is unavoidable, organizations need to equip their remote employees with tools that let them painlessly back up all important data and restore it with a few clicks.
The 3-2-1 backup strategy provides a great place to start, recommending the creation of 3 copies of all data, stored in at least 2 types of storage media, with 1 copy stored at an offsite location.
In practice, remote employees can follow the 3-2-1 backup strategy by having one local copy of work-related data stored on the main system drive, another one stored on an external hard drive, and the third one kept in the cloud, whose numerous benefits include limitless scalability and instant availability.
7. Equip remote employees with data recovery software
Even with a tried-and-tested backup strategy in place, there’s still some room for data loss to occur. In most cases, you can recover lost files without much effort, but only when the recovery process isn’t delayed.
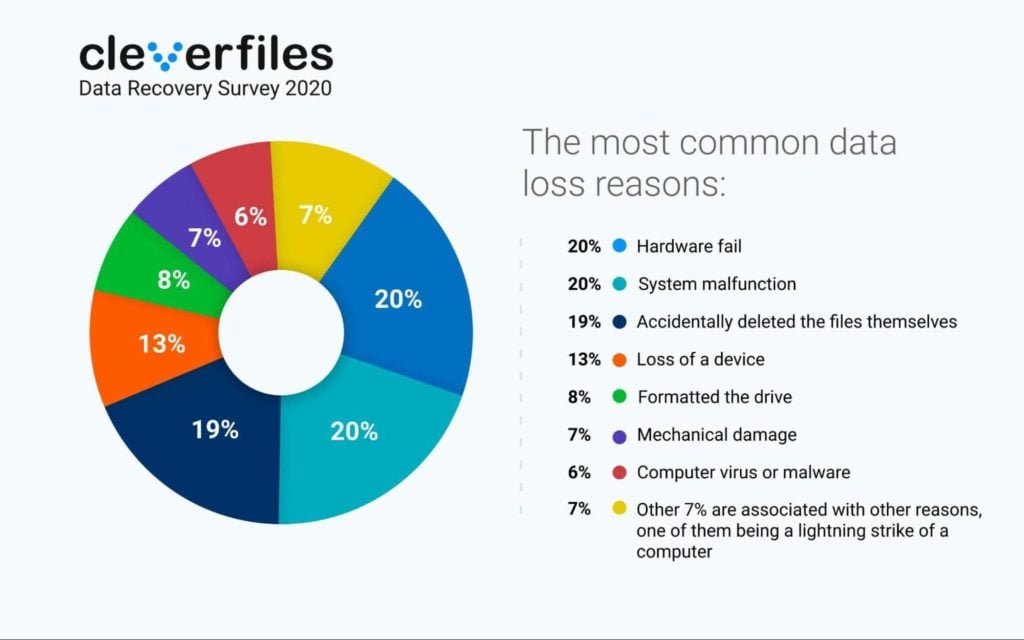
That’s why employees should be equipped with data recovery software that empowers them to undelete lost data with a few simple clicks and without any special knowledge. The best data recovery software applications available today can recognize hundreds of file formats, including Microsoft Office documents, PDFs, and file archives.
While the specific data recovery algorithms can vary greatly from one solution to the next, the process itself is usually very similar:
- Scan the storage device the lost files were on.
- Wait for the data recovery software application to find all recoverable files.
- Select your files and recover them to a safe destination.
From start to finish, data recovery can take as little as a few minutes—it all depends on the size and speed of the storage device being recovered.
8. Improve your password security
Alarmingly, about 80% of data breaches are still caused by weak passwords, even though experts have been preaching the importance of password best practices for ages. The problem is that many organizations are stuck in the past when it comes to their understanding of how strong passwords and password management practices look like.
Instead, it’s much better to request employees to change their passwords only when there’s a reason to believe one or more passwords have been compromised. When that happens, employees should be allowed to generate a new password
What’s just as bad as relying on outdated password management practices is not taking advantage of modern authentication methods, namely multi-factor authentication (MFA), which can protect employees from an unknown person trying to access their data by requiring two or more verification factors to be provided.
The verification factors can be:
- Knowledge (something only the user knows) – a password or PIN
- Possession (something only the user has) – a badge or smartphone
- Inherence (something only the user is) – fingerprints or voice recognition
According to Microsoft, MFA can prevent up to 99.9 percent of automated attacks, so enabling it should be an absolute no-brainer, especially considering that it doesn’t cost almost anything to implement.
9. Shine light on shadow IT
Shadow IT involves the use of information technology systems, devices, software, applications, and services without explicit IT department approval.
The massive global shift to remote work has fueled the growth of shadow IT in many organizations, as individual employees and entire departments have taken matters into their own hands and started using all kinds of tools—from instant messaging applications to employee engagement software—in order to remain productive.
However, shadow IT is a major threat that can easily lead to organization-wide data breaches. When the IT department isn’t aware of the existence and use of certain software applications and hardware devices, it can’t take the proper steps to secure them.
The solution isn’t to forbid employees from using the tools they like the most. The solution is to bring their tools of choice to light so they can be properly secured and licensed. When employees are allowed to influence their organization’s IT choices, everyone benefits because innovation can happen organically, driven by real needs and requirements.
10. Don’t forget about physical security
Physical security can easily become an afterthought when working from home. After all, most people consider their home to be the safest place in the world. Unfortunately, thieves, just like cybercriminals, are opportunistic creatures, and they don’t hesitate to take advantage of the fact that remote employees are typically equipped with fairly expensive work computers and smartphones.
One of the simplest things you can do to keep business data secure when your employees work remotely is to remind them to keep their doors locked all the time. Jobless thieves have plenty of time to wait for the right moment to strike, and they don’t need more than a moment to grab the first electronic device they see and run away with it.
You may also want to consider offering financial help to employees who would like to purchase a home security system, especially those who are likely to work remotely long-term. Even a few smart cameras can go a long way in acting as a powerful deterrent.
Conclusion
Many remote jobs that have been created by the COVID-19 pandemic are here to stay, and so are the data security challenges associated with them. The 10 methods described in this article provide a foundation for strong cybersecurity defenses by addressing digital and physical threats alike.
Originally published Nov 05, 2020, updated Apr 17, 2023




