Worried about cybersecurity at your small business? That makes sense. According to a recent study, nearly half of all cybersecurity attacks target small businesses.1 Successful cyberattacks could cost hundreds of thousands of dollars, which could be the end of any small business.
It seems as if there’s a new kind of cybersecurity threat to worry about every month. The good news: every new kind of cyberattack, a new and improved cybersecurity plan is also crafted to combat them.
But it can be overwhelming to figure out where to focus your limited resources when it comes to protecting your business online. Let’s look more closely at these threats and which ones small businesses, especially, should watch out for.
Today, we’ll cover:
- Cyber threats that impact small businesses
- How to tell if your business is at risk
- Who can help protect your business from cyber attacks
- How to protect your business on your own
- How to protect your business with a security provider
Not a cybersecurity expert? See how the right partner can keep your business safe.
What kind of cybersecurity threats do small businesses face?
A small business has to be ready to face several kinds of attacks. For example, at any given moment, your business could become the target of a ransomware attack, phishing scam, or data breach—and that’s without accounting for the other types of scams that are out there.
These scams and attacks tend to have a few set targets. Often, cybercriminals try to get access to your customers’ sensitive information, which negatively impacts your customer relationships, since it decreases trust in your business.
In order to prevent these criminals from successfully stealing your customers’ information, you should always make sure you’re using software that provides you with top-of-the-line infrastructure security, like RingCentral does.
Cyberattacks may also be aimed at your business’s sensitive data, including financial details and/or employee information.
In other words, small businesses have to deal with a whole host of cybersecurity risks.
Is my business at risk for cybersecurity threats?
Put simply, any small business is constantly at risk, although nearly every incident can be avoided with a well-chosen cybersecurity solution.
The more active your business is on the internet, the greater the risk you face. This is especially true if you regularly use social media platforms like TikTok, Twitter, or even LinkedIn. Social media scams are only on the rise, meaning businesses have to be extra careful.
This might make the situation look a little bleak, especially for startups, which typically rely heavily on social media marketing to find their audiences.

However, just because there are more cyberattacks on social media users now doesn’t mean you can’t protect your business (and yourself) from those attacks.
Once you know on whom you can rely to keep your business safe from malware, you’ll be able to formulate a strong cybersecurity strategy.
Who protects your business from cyberattacks?
There are two main forces that make up the bulk of the general defense against cyberattacks.
One of these is made up of governmental organizations dedicated to protecting businesses and individuals from cyberattacks. The second consists of cybersecurity software providers.
The government
Government agencies like the Department of Homeland Security (DHS) are dedicated to protecting American citizens from all kinds of internet-based scams, including cyberattacks.
The Federal Communications Commission (FCC) also has a Cybersecurity and Communications Reliability division, which works on both monitoring and preventing cybercrime.
As of 2012, the FCC has declared that “theft of digital information has become the most commonly reported fraud.” This shows how seriously they take data loss and breaches.
When you’re constructing a plan to protect your business, it’s important to ensure that you follow any cybersecurity tips put out by the DHS, FCC, and any similar governmental bodies. Their guidelines should form the basis of your cybersecurity strategy.
Cybersecurity software providers
If governmental guidelines make up the bones of a cybersecurity plan, security software providers are the meat.
One example of a type of security service that exists to fend off cyberattacks is antivirus software. This can help you maintain your data security even in the unlucky event that you’re sent phishing emails, and interact with their content.
RingCentral offers seven layers of security built into its software, to cover the needs of any small business:
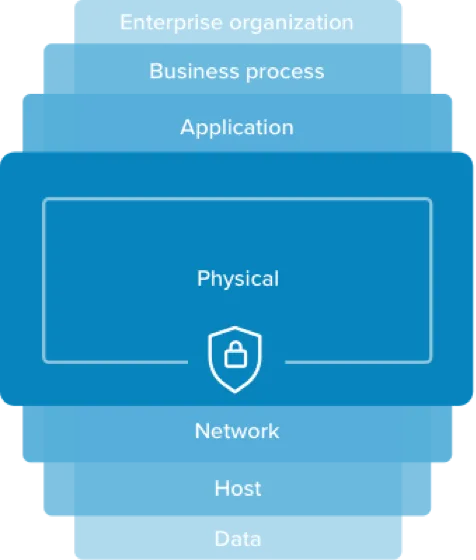
This multi-layered approach to cybersecurity protects all of your business communications in RingCentral from phishing, pharming, spam, and other types of scams.
How to protect your business on your own from cybersecurity threats
There are two key ways to protect your business from cyberattacks: on your own and with the help of experts and specialized software. Of course, the latter can do significantly more, though both are important in creating a bulletproof plan.
1. Strengthen your existing security systems
What’s the point of locking your data behind password protection if your password is easy to guess?
Using passwords is a good idea. Using complicated, strong passwords that are very difficult to work out without spending a lot of time guessing can be the thing that saves you from a successful cyberattack.
When it comes to passwords, it’s important to buy yourself as much time as possible. If a hacker can guess your password in a few hours, you’ll have a few hours to realize something has gone wrong. That’s why you should always update your passwords.
The same logic applies not only to your cyber security but also to the physical security measures you’re already using.
If you’ve got a firewall, check to make sure it’s a strong one that covers the full extent of your offline data. Ensure you’re making regular data backups, so that if something happens and the servers need to be wiped, it doesn’t spell disaster for the business.

2. Store your sensitive information offline
As a small business, you’re more likely to be the target of cybercrimes. That’s why you’ve always got to be prepared for the worst-case scenario.
One way of doing this is by ensuring that your most important information won’t be available to hackers even if they do get access to your devices.
Never store your credit card details in your browser, or anywhere else that hackers would be likely to look. If you need to store this information on a device at all—for instance, if you’re using a company card and don’t always have physical access to it—make sure it’s password protected.
3. Train your entire team on cybersecurity risks
It’s not just your IT person who should know how to stop cyber threats before they happen. With attacks like phishing and smishing, employees are targeted and asked to give their login details so an outside person can access sensitive information. This is why everyone on your team needs to know what these attempts look like and what to do when they occur.
How to protect your business with a security provider
1. Secure your network
A firewall is one way of going about this, though professional software will offer a host of options to help improve your network security.
The software you use in other business areas must take cybersecurity into account, too.
RingCentral’s communications solutions boast a seven-layer security system is a great way to protect your network while collaborating with colleagues, sharing files with clients, and all those other business-critical activities.
2. Get a VPN
Virtual private networks (VPNs) make it more difficult for hackers to track your IP address. This adds some extra protection—which is made even more powerful since RingCentral can work with VPNs to further enhance your security measures.
3. Add layers of authentication
As mentioned earlier, passwords can be guessed or figured out. This is unfortunately even true for the best passwords.
That’s where multi-factor authentication comes in.
This security layer requires multiple endpoints, such as verification from an email, text, or phone call, to make sure the person accessing the information is you. It’s especially useful during situations like the pandemic, when everyone is working in distributed teams and has easy access to their own mobile devices in addition to their work laptop or desktop computer.
RingCentral’s multi-factor authentication options work with all operating systems, making it a perfect choice for working from anywhere. Read more about how we protect your business communications at every step.
4. Choose the right software providers
Every service provider offers a different set of features to protect your business. It’s important to know what you need and to what extent a given provider can offer that.
When you choose RingCentral, you’re opting for powerful security features that offer top-quality protection to all devices associated with your business.
RingCentral guarantees the most secure business communications. This is especially important, as it enables you and your team members to work from anywhere, anytime, knowing that your security needs are entirely taken care of.
Cybersecurity in a small business: The right partners make it simple
Hopefully, our cybersecurity tips have provided you with some useful insights and suggestions to keep your business secure against cyber threats.
All this might seem like rather a lot to take in, but by learning about the basic principles of cybersecurity you’ve taken a big step in the right direction. Fairly basic security measures can do a lot to protect your business from the threats that are out there—and your clients will thank you for it.
- “Cyberattacks now cost companies $200,000 on average, putting many out of business.” CNBC. https://www.cnbc.com/2019/10/13/cyberattacks-cost-small-companies-200k-putting-many-out-of-business.html
Originally published Jul 19, 2022, updated Nov 20, 2023





