Updated Apr 2020
While video conferencing is not a new technology, the entire world is now learning to find creative ways to continue being productive while not being able to be physically in the same room (hello, social distancing).
Teachers have taken to virtual classrooms, healthcare providers are using video calls to provide telehealth, friends are sharing links in order to share time, and the world is learning to move forward, even when we can’t be together.
In a time where it’s not only good, but also necessary to be an early adopter to new technology, one conferencing platform that received initial attention was Zoom.
But like all technologies, video conferencing has its hiccups. It was only a matter of time until hackers and people with too much time on their hands found a way to turn something good into something gross.
Enter “Zoombombing.”
There’s lots of video conferencing software out there, but much like most of us now know what it is to “Uber home” even when we’re using a Lyft, it’s become clear that “Zoombombing” isn’t limited only to, well, Zoom.
In this post, we’ll look at:
- What exactly Zoombombing is
- The response to Zoombombing so far
- The 6 Dos and Don’ts of video conferencing
🤔 What are some affordable Zoom alternatives? Check out this free comparison chart.
So what is Zoombombing?
Basically, Zoombombing is an unwanted interruption of a video conference call that causes disruption and confusion. It can be jarring, annoying, and sometimes downright traumatizing—and most importantly, it invades the users’ privacy and security.
Now that the security of these types of softwares have been called into question, the WFH world is asking, “How do I keep these meetings free from unwanted outsiders?”
What has been the response to Zoombombing?
In an interview by ABC News, Brad Garrett, a former FBI agent, said Zoom has been a rich target for cyber criminals and malicious actors.
“Cyber criminals are targeting video conferencing sites like Zoom, particularly during the COVID-19 pandemic,” Garrett, now an ABC News contributor, said. “Typically they create domains that impersonate Zoom, with the goal of stealing personal information.”
He noted that because about 60% of Fortune 500 companies use apps like Zoom, cyber criminals see an opportunity to potentially steal corporate proprietary information and sensitive information about employees.
“As more schools and businesses work remotely, this creates an ideal environment for cyber thieves,” Garrett said.
No matter what video conferencing or screen sharing software you’re using, everyone is susceptible to having their video conferences hacked, so here are a few ways to safeguard your meetings so that this doesn’t happen to you (and one reason why RingCentral would be a great fit for your video conferencing needs).
The 6 Dos and Don’ts of video conferencing security
1. DO password protect your meetings
While it’s a good first step to not post your meeting links to a public forum, you could go a step further and protect the meeting with a specific password or meeting ID.
For example, in RingCentral Video, you can set these options right when you schedule a new meeting:
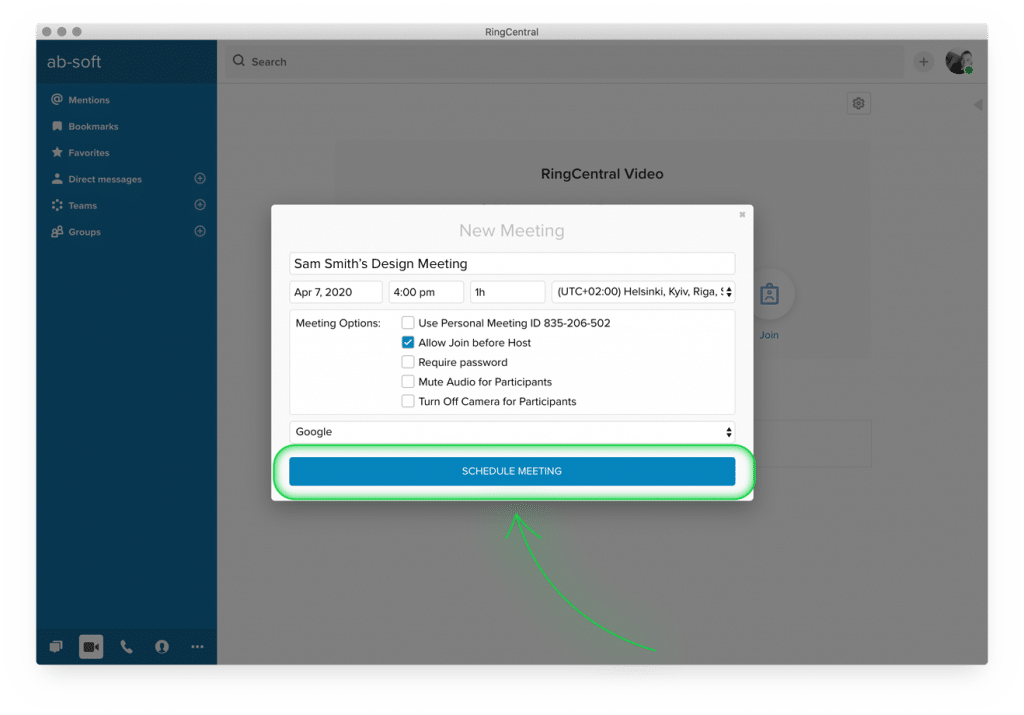
This way, someone has to know your meeting ID and the password—both of which are completely unique to your meeting—to get in.
The password should be sent out ahead of time to all participants and chosen by the organizer. If the meeting is recurring, you don’t necessarily have to use a new password every time, but it would certainly help you keep the conference secure. See this in action by getting a product tour.
2. DON’T allow anyone and/or everyone to screen share
Again, another handy security feature built into most video conferencing software is the ability to share screens with one another. This feature is helpful to those needing to present different statistics or teach a new idea, but it’s also a way for predators to take over the meeting.
By limiting screen sharing or even allowing only the host to control the screen, you can minimize the chances of someone posting inappropriate stuff or annotating in unseemly ways.
3. DO lock the meeting once everyone’s arrived
This is just a good habit to have—once all your attendees are in the meeting, some video conferencing software will let you lock it so that strangers can’t stumble in:
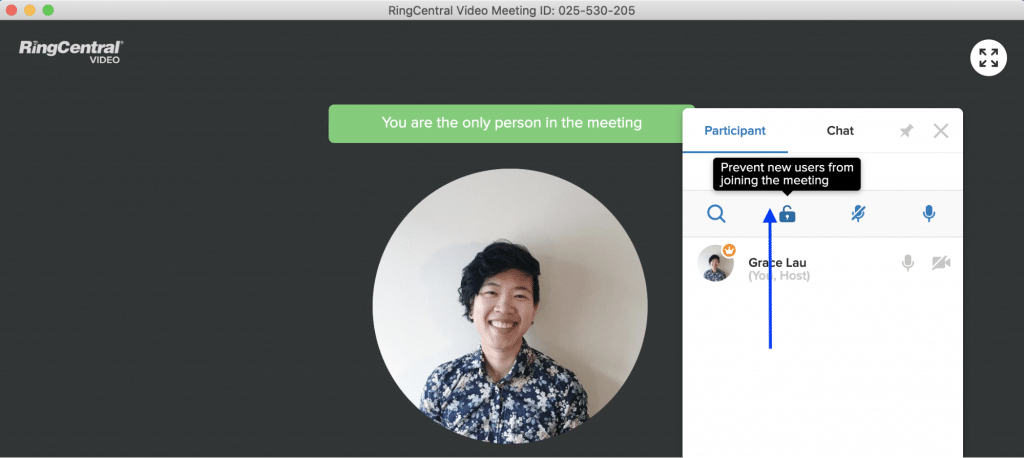
Locking a meeting in RingCentral Video
4. DON’T share meeting links on social media
While social media has helped businesses market their goods and keep friends and family connected, it also leaves people vulnerable to having anything they put on the internet read by literally anyone.
For example, as Von Glitschka states from an interview with CNBC, he “was just trying to teach people how to create designs in Adobe Illustrator.”
“Glitschka, half of the two-person design firm Glitschka Studios in Salem, Oregon, had shared the link to his Zoom video call on his Facebook, LinkedIn, and Twitter profiles on Saturday, and a dozen or more people tuned in.”
Glitschka’s conference was gatecrashed by an individual shouting racist slurs, causing him to have to shut the entire conference down. He no longer shares these links online, but invites anyone wanting to tune in to direct message him so that he can send the info directly to anyone interested.
It seems like a simple tactic, but keeping these conference links private and sharing them only with those you are wanting to allow into the meeting is an effective way to keep your conferences from being taken over by someone with an alternative agenda.
To go a step further, we’d suggest only sharing the link for the conference a little before the meeting is supposed to start. If you send out a link an hour before the meeting is set to begin, you’re giving hackers less of a window to find that sensitive information.
5. DO review the other security settings
In an era where we are quick to hit “I accept” when our devices ask if we’ve read and reviewed the privacy settings, it’s now more important than ever to take a few moments to familiarize yourself with how video conferencing works and which tools are built in to already keep you safe when in a meeting.
Most video conferencing platforms have comparable security settings: the ability to turn screen sharing off and on, allow the use of waiting rooms, etc. But it’s important to know how to use these settings before jumping into the first meeting. Familiarizing yourself with a few security tools will only contribute to the overall security of each meeting you hold.
6. DO consider tools that come with security features
Using a tool that’s well known may seem like the obvious choice, but it can also be a bit of a double-edged sword.
Zoom is used for not only business meetings, but also parties, family get-togethers, and really any random gathering that people are wanting to throw together. Popularity naturally makes it a bigger target, and if you’re hoping to get business done, using the tool that’s so heavily in the press may not be the best option.
On the other hand, as a more business-focused platform, RingCentral Video comes with many of the features we mentioned above, like controlled annotations, password-protected meetings, and industry security standards likewebRTC—without the same level of mainstream attention from bored teenagers and hackers.
Learn more about RingCentral’s Video’s security features and what it’s doing to protect customers’ privacy, such as not routing meetings through servers in China or sharing information with Facebook.
The bottom line for not getting Zoombombed
The fact is that this can happen to anyone, whether you’re using Zoom or a Zoom alternative, but that doesn’t mean that we should live in fear of using technology. Video conferencing is a communication tool, and like all tools, it’s best to know how to use it securely.
To summarize it all up, make sure to always reach out if you do notice any suspicious activity (like people with names you don’t recognize joining your meeting), keep your meeting links confidential, and review the security settings in order to know the best way to protect your (and your coworkers’) safety when working remotely.
🕹️ Get a hands-on look at how RingCentral works by booking a product tour:
💰 You can also use this calculator to see roughly how much your business could save by using RingCentral to support your team’s communications with clients, customers, and each other.
Originally published Apr 28, 2020, updated Jun 17, 2022