The global VoIP market is projected to grow from over $145 billion in 2024 to over $326 billion by 2032. This means more businesses are making the transition to Voice over Internet Protocol (VoIP).
Businesses do it for different reasons, including cost savings, increased productivity, and advanced capabilities. However, newer technologies also present new security vulnerabilities.
VoIP critics cite cybersecurity threats as the main concern. In this guide, we’ll cover the VoIP security risks you need to mitigate to protect your business and its customers.
What are VoIP security risks?
VoIP security risks are any threat or vulnerability associated with any paid or free VoIP phone systems. Because you use the internet to make calls, hackers and scammers can find ways to intrude and steal information.
Threats include social engineering, call tampering, malware, and Distributed Denial of Service (DDoS) attacks. Common causes of unauthorized access include:
- Poor password policies
- Minimal network controls
- Few to no encryption layers
These and other threats make it vital to protect your data and that of your customers.
Why is it important to mitigate security risks for your VoIP network?
The VoIP benefits outweigh the drawbacks as long as you minimize the risks. Let’s examine how VoIP works to understand the importance of threat mitigation.
VoIP makes calls over the Internet using technologies like Session Initiation Protocol (SIP). The system converts voice into digital packets, transmits them across the web at light speed, and unpacks them into audible speech at the recipient’s device. For both participants, the experience mirrors a traditional phone call.
Imaged sourced from RingCentral
Digital phone calls create numerous entry points for cybercriminals to exploit. Hackers can listen in, hijack calls, or access your entire phone system. VoIP providers continuously evolve their security measures. However, criminals are always searching for new vulnerabilities.
According to IBM, the average cost of a data breach was $4.88 million in 2024. These costs include compliance penalties and legal consequences. However, they don’t account for long-term reputational damage and lost business opportunities.
Besides financial implications, other factors to consider are:
Business continuity: Communication is mandatory for operations. If your phone system goes down or malfunctions, you’re wasting time, money, and valuable resources.
Data protection: You handle sensitive information such as financial data and confidential discussions. Malicious actors can sell or leak this information, damaging your reputation.
Customer trust: One security lapse or data breach can result in a huge amount of negative PR. Failure to protect customer data can result in irreparable damage to your reputation. Existing customers may leave, and potential leads will flock to more trustworthy brands.
7 VoIP security risks to address immediately
A VoIP phone system helps your business move into the digital age. It frees you from copper wires and expensive equipment and streamlines incoming and outgoing call management.
If you want to protect your business and its customers and get the most from IP telephony, you’ll need to be aware of the following security threats.
1. Phishing
Phishing is when scammers send emails or other messages pretending to be a reputable source. They are often “fishing” for account credentials.
A 2023 survey found that nearly 70% of IT professionals have encountered vishing attacks. What are vishing attacks? They’re phishing attempts made with VoIP calls and voice messages. It’s often the gateway for VoIP breaches, working in tandem with other methods.

Cybercriminals often impersonate IT support, suppliers, service providers, or company higher-ups. The goal is to trick employees into giving out login credentials or granting access to restricted systems.
Vishing may also attempt to gain bank details for your team members or the company.
Once malicious actors have access, they can eavesdrop to gain access and steal sensitive data from your organization. The possibilities are nearly endless once they gain entry into admin portals.
Multi-factor authentication restricts access by requiring users to provide two or more verification credentials, such as a password and a code sent to a mobile device.
Immediate action item: Deploy multi-factor authentication (MFA) across all VoIP accounts.
2. Spoofing and call tampering
Unlike phishing, which relies on deceptive messages, spoofing directly manipulates call identification systems. In VoIP, this is often accomplished by caller ID spoofing and/or using recorded voice messages known as “robocalls.”
Team members recognize the number and name, trusting whoever is on the other end of the line. Once spoofers steal the information they need, they can bypass security measures and cause major damage.
Immediate action item: Enable caller verification protocols and implement real-time monitoring of robocalls and call patterns.
3. DDoS attacks
Distributed denial of service attacks have been taking websites down for decades. However, they can also target your VoIP phone service, overwhelming servers and using up all of your bandwidth. Your communications will lag or go completely down, crippling business operations.
People won’t be able to reach your sales and support teams. Frustrated customers will lose faith in your company. Simultaneously, your team will be unable to perform necessary tasks. You’ll likely miss out on revenue-producing opportunities.
Today, modern DDoS attacks are easy to coordinate using sophisticated botnets and AI. Unlike other threats, DDoS attacks focus purely on disrupting your business.
Immediate action item: Deploy DDoS mitigation tools and establish network redundancy protocols.
4. Traffic interception and call tampering
Traffic interception is when hackers use unsecured networks to intercept unencrypted VoIP traffic. They can even do this for streaming media such as video. Once intercepted, they can eavesdrop and record data from the meeting.
Two traffic interception methods are:
- Spam over Internet Telephony (SPIT): Automated spam calls that redirect to international and premium numbers
- Voice over Misconfigured Internet Telephones (VOMIT): Hackers lift voice packets from calls.
Call tampering turns the threat dial up to 11. Attackers can hijack calls, alter voice packet data, or route calls to premium numbers. The latter allows scammers and local telecom providers to share the spoils.
Call tampering victims may also experience poor call quality and dropped calls. This threat builds on vulnerabilities exposed by other methods, such as spoofing.
Immediate action item: Implement end-to-end encryption protocols and conduct a network security audit.
5. Malware and viruses
Malware threatens any system with internet access. VoIP-specific malware targets vulnerabilities in communications systems, web browsers, mobile apps, and softphones. Once installed, they steal sensitive data, manipulate calls, or gain system control.
Malware comes in many forms, such as:
- Viruses: attach to other files and execute malicious code if opened
- Ransomware: encrypts and locks data until a payment is made to the hacker
- Trojans: malware disguised as legitimate software
- Mobile malware: designed to target mobile devices and their specific vulnerabilities
Malware can steal passwords and create backdoors for hackers to attack. Many of these malicious applications can quickly spread through your network. If one employee downloads some malware, it can wreak havoc on multiple systems and devices.
Immediate action item: Install VoIP-specific security software and establish regular update schedules.
6. Toll fraud and theft of service
Toll fraud is when someone gains unauthorized access to your phone system. Once inside, they make numerous fraudulent calls to expensive premium-rate phone numbers.
Victims often only discover the fraud after experiencing bill shock. At that point, it can be difficult to avoid paying the toll charges.
Toll fraud, along with traffic interception, is often part of what’s known as International Revenue Sharing Fraud (IRSF). Small carriers work with scammers to help steal your money.
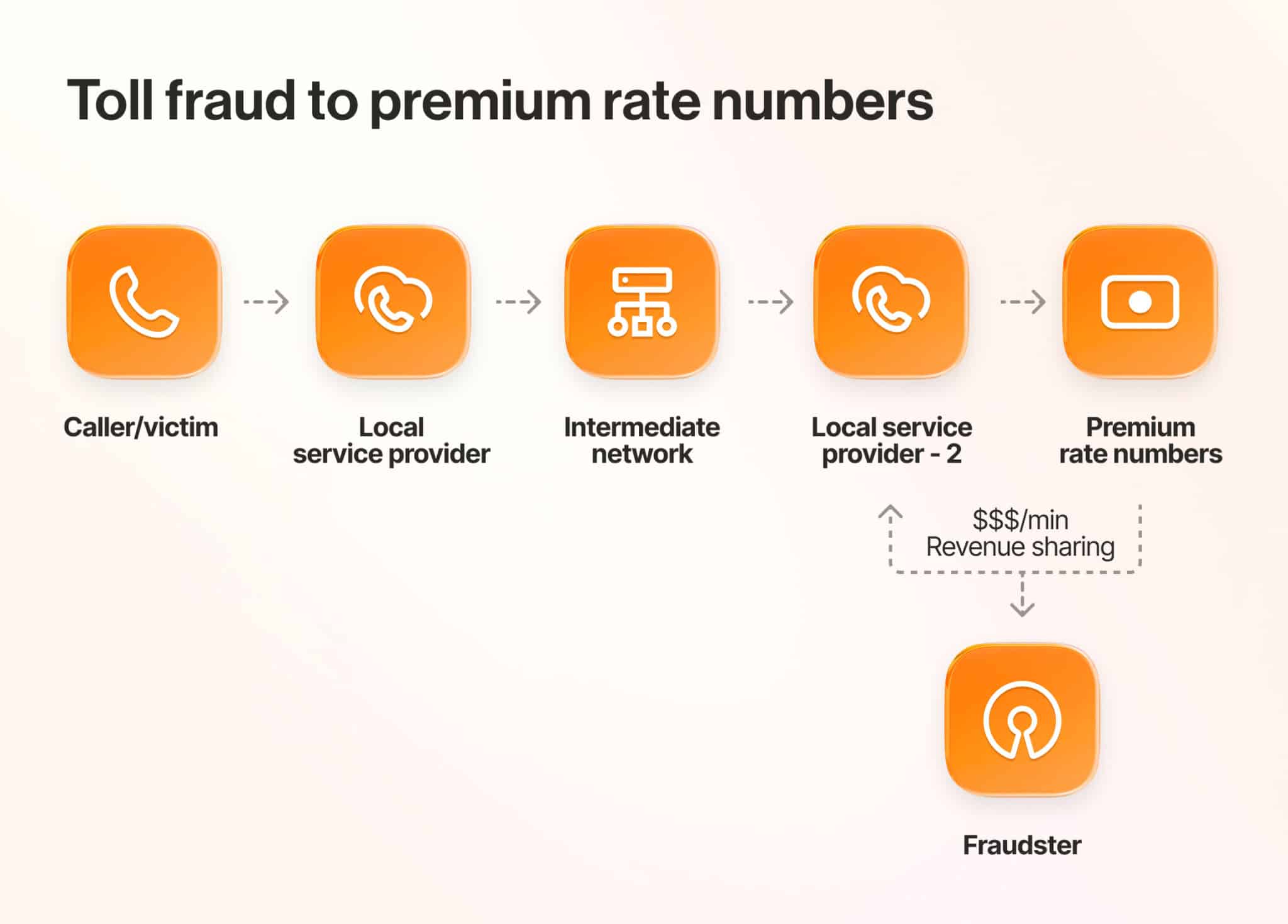
Cybercriminals use social engineering techniques, such as phishing or exploiting system vulnerabilities, to access your critical communications network. With calling access, attackers can make unlimited fraudulent calls.
With toll fraud, hackers may gain access to your VoIP phone system for their own use. In this case, they use your service without paying, stealing bandwidth. They may also call risky numbers and extensions.
Immediate action item: Set up call monitoring and access controls for international calling.
7. Unauthorized access and network breaches
Sometimes, criminals gain access through simple means. Vulnerabilities can range from weak and obvious passwords to out-of-date networks.
Unauthorized access may even occur on-premise with disgruntled or malicious employees. Once they’ve exploited an oversight, the world is their oyster. Customer data, sensitive company information, and financial accounts are all up for grabs.
Immediate action item: Enforce strong password policies and isolate your VoIP network from other systems.
Best practices for mitigating security risks
VoIP security threats are no joke. However, following best practices can help minimize the risk to your business.
Strong password policy
The first line of defense is a strong password policy. Passwords should be 12–16 characters and combine letters, numbers, and symbols.
MFA is also a non-negotiable for protecting system access. Ensure that passwords are changed regularly and never repeated. When someone leaves the company, revoke their credentials immediately.
Use call and data encryption
Enable end-to-end encryption (E2EE) for all voice and media traffic. VoIP solutions like RingCentral use Transport Layer Security (TLS) and Secure Real-time Transport Protocol (SRTP).
These technologies protect your calls from eavesdropping and interception.
Configure firewalls
Use firewalls to monitor and direct VoIP network traffic. Use filters to block suspicious IP addresses and enable any built-in intrusion alert systems. (Consult your provider to open specific ports so you don’t affect performance.)
Update everything
The best way to stay one step ahead of malware is to have everything up-to-date. That means every operating system, application, device, and piece of network equipment should be current. Add mandatory, regular software and firmware updates to the calendar for all team members.
Choose the right VoIP provider
Save stress by picking a reputable VoIP provider. Platforms like RingCentral feature sophisticated security measures, such as robocall mitigation and spam blocking. Our service also meets SOC 3, GDPR, ISO 27018, and Fedramp compliance requirements.
Train your team
Training your team to spot social engineering goes a long way toward thwarting cybercriminals. Ensure that you have effective communication channels in place and include procedures for reporting suspicious activities and breach incidents.
Perform regular security audits
Hackers are always upping their game. Security audits keep your system on its toes, assessing for vulnerabilities. Schedule comprehensive audits for early issue detection and action planning.
Secure VoIP to protect your business
There are so many reasons for your business to use VoIP. Don’t let the threat of scammers and cybercriminals deter you from flexible, cloud-based phone systems. Be aware of potential dangers, be proactive, and minimize, if not eliminate, their threats.
Understand the threats in this list and take the necessary precautions. Develop strong VoIP security policies, use the right tools, and constantly refresh your tactics.
You’ll prevent potential disruptions and protect your customers’ data. You’ll also get to enjoy the seamless benefits of a business VoIP system.
FAQs
Is it safe to use VoIP?
Yes, VoIP is safe. Users only need to be aware of the potential risks of virtual communication, such as phishing and traffic interception.
Understanding the risks guides you to take the necessary precautions. Using a reputable, secure provider, such as RingCentral, helps streamline VoIP security.
What are the common VoIP security risks?
Common VoIP security risks include social engineering attacks such as phishing and spoofing. Users gain access to VoIP systems with fraudulently gained or forged credentials.
Other VoIP threats include malware infections, DDoS attacks, traffic interception, and call tampering. Configuring your network, training your team, and using a secure VoIP solution help mitigate these security risks.
Originally published Jul 23, 2025