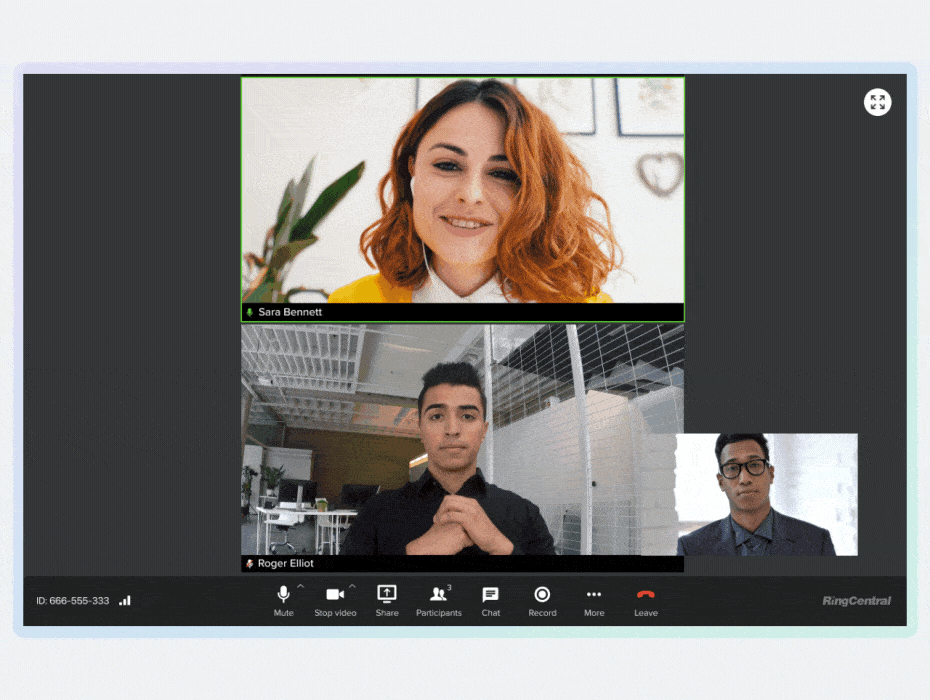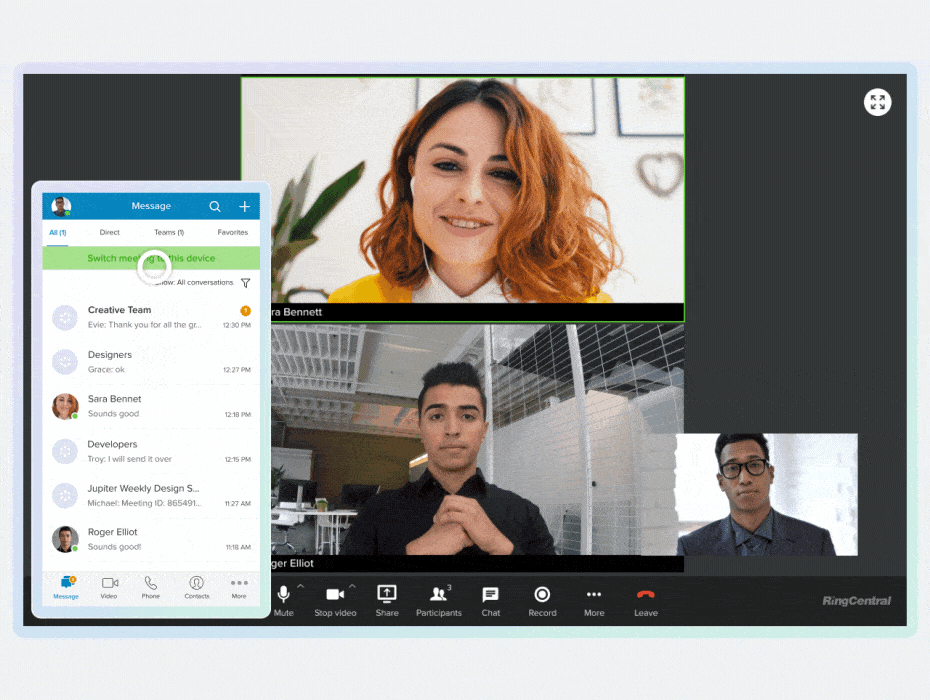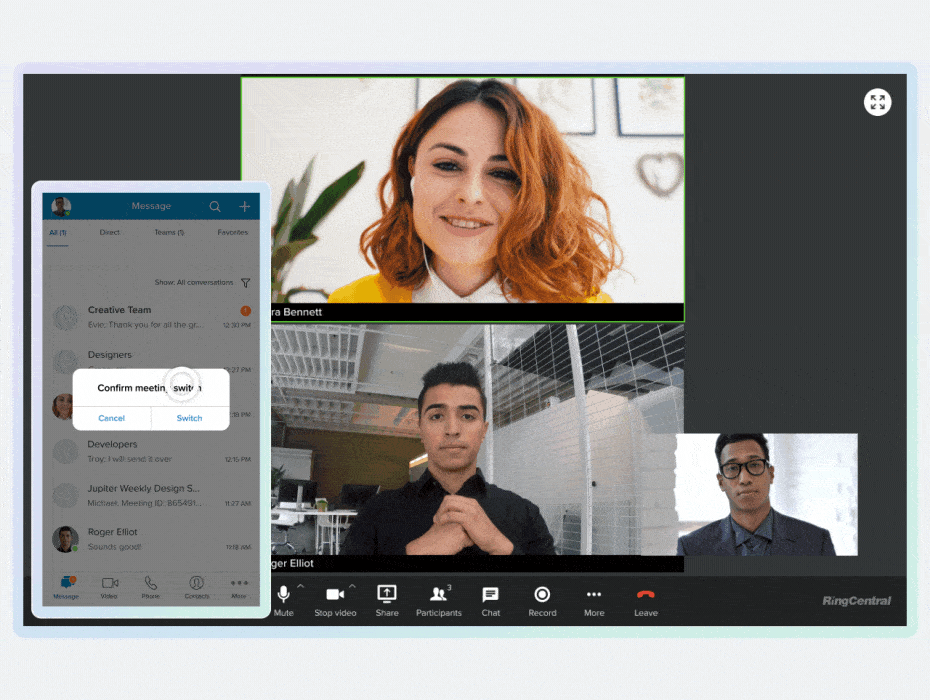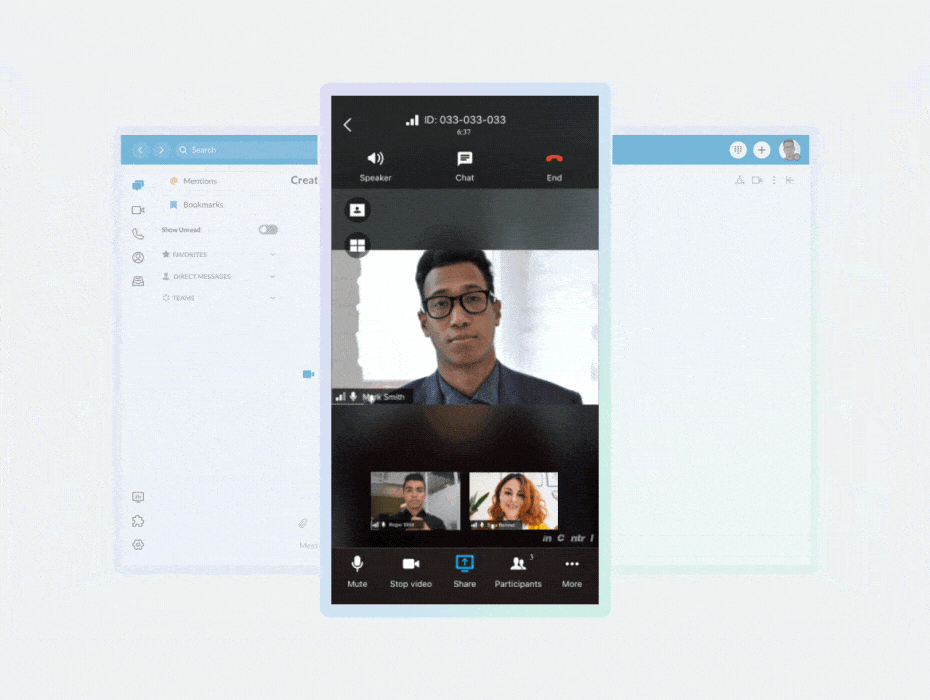
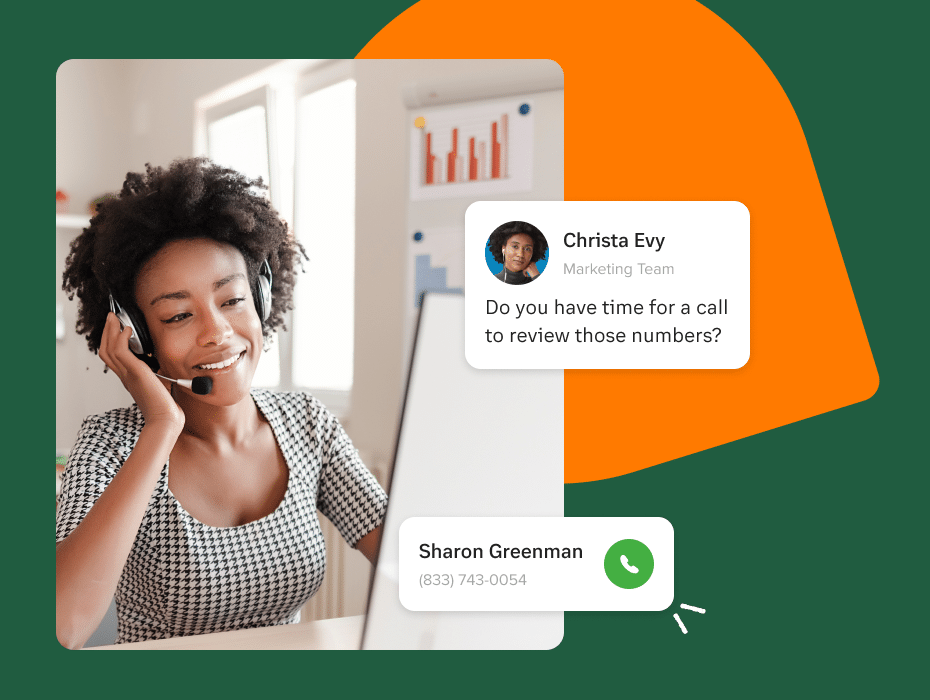
At RingCentral, we maintain a long-standing commitment to security—built on a deep expertise in operating and securing unified communications and SaaS products.
Security is in our DNA. We take a multi-dimensional approach to put the safety of your data first by applying best-in-class technologies and rigorous processes.
⭐ Want to learn more about UCaaS security? ⭐
Here’s what to look for in a UCaaS provider’s security posture.
Here are a few ways RingCentral helps IT organizations navigate security concerns in today’s hybrid workforce with built-in controls designed to protect their employees and organizational data.
1. Mobile application management
Today’s work environment is more mobile than ever, which means UCaaS solutions must meet the needs of an increasingly hybrid and remote workforce. This also poses new security challenges with employees bringing their work devices everywhere they go.
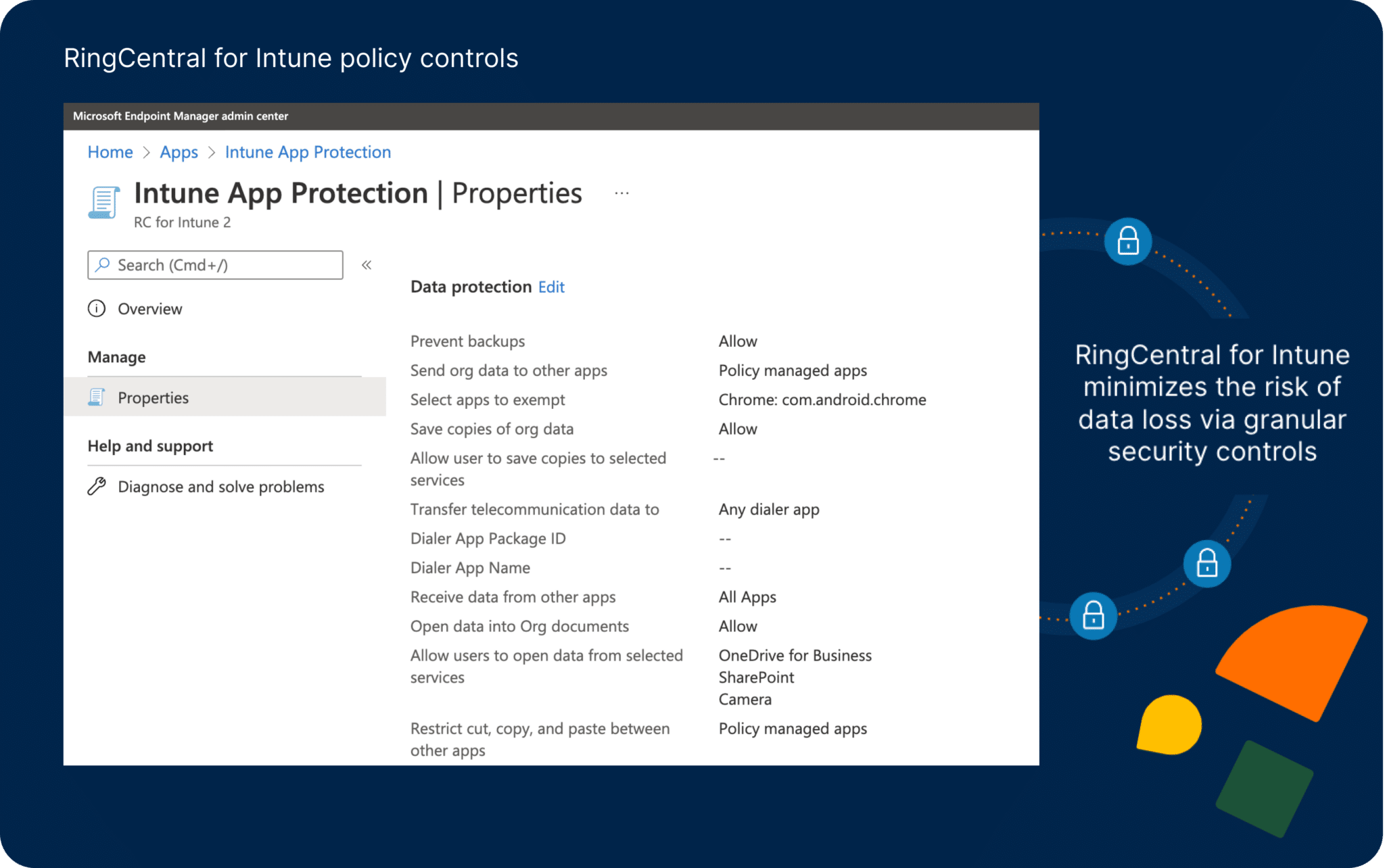
Our new integration, RingCentral for Microsoft Intune (iOS, Android), makes it easy for IT to monitor and enforce security policies on the RingCentral app across company-owned and bring-your-own-device (BYOD) environments.
With RingCentral for Intune, IT teams can:
- Minimize the risk of data loss
- Access granular security controls
- Centralize security policy controls on all managed and unmanaged mobile devices
Here are a few examples of how RingCentral for Intune can manage devices and protect corporate data:
- Disable copy and paste from RingCentral into any non-managed, 3rd party app.
- Block all jailbreak devices from logging into RingCentral.
- Encrypt data that is stored in the RingCentral app to avoid access by non-managed, 3rd party applications.
- Disable file sharing (files, messages, contacts, photos) with other applications.
- Remove data where once the user is logged out or unenrolled, the application data is wiped off.
The new RingCentral for Intune app is available on the Apple App Store and Google Play Store. Existing customers can contact RingCentral support to activate.
2. Account access restrictions
Guarding against unwanted data loss and exfiltration of information is top of mind for IT security departments. One of the ways RingCentral gives IT the tools they need is by securing against unauthorized account access to the RingCentral MVP desktop and web app.
This control prevents users from logging into unauthorized personal accounts and exfiltrating sensitive data while on a corporate network.
For example, if an employee attempts to login to RingCentral desktop app via an unapproved personal account (namely, an account other than the corporate domain. For example, @gmail.com), the employee will be unable to access RingCentral.
3. Authenticated sign-on

RingCentral Single Sign-On (SSO) integrates easily with any identity provider (IdP) that supports SAML 2.0, such as Okta, OneLogin, Ping Identity, Microsoft Azure Active Directory, Google Workspace or your homegrown IdP.
Our integrations provide secure identity management and supports automated user provisioning and deprovisioning in real-time. This allows IT to easily manage any employee’s access to the RingCentral MVP app, providing employees with a secure connection no matter where they work.
4. Advanced Compliance Monitoring via Theta Lake
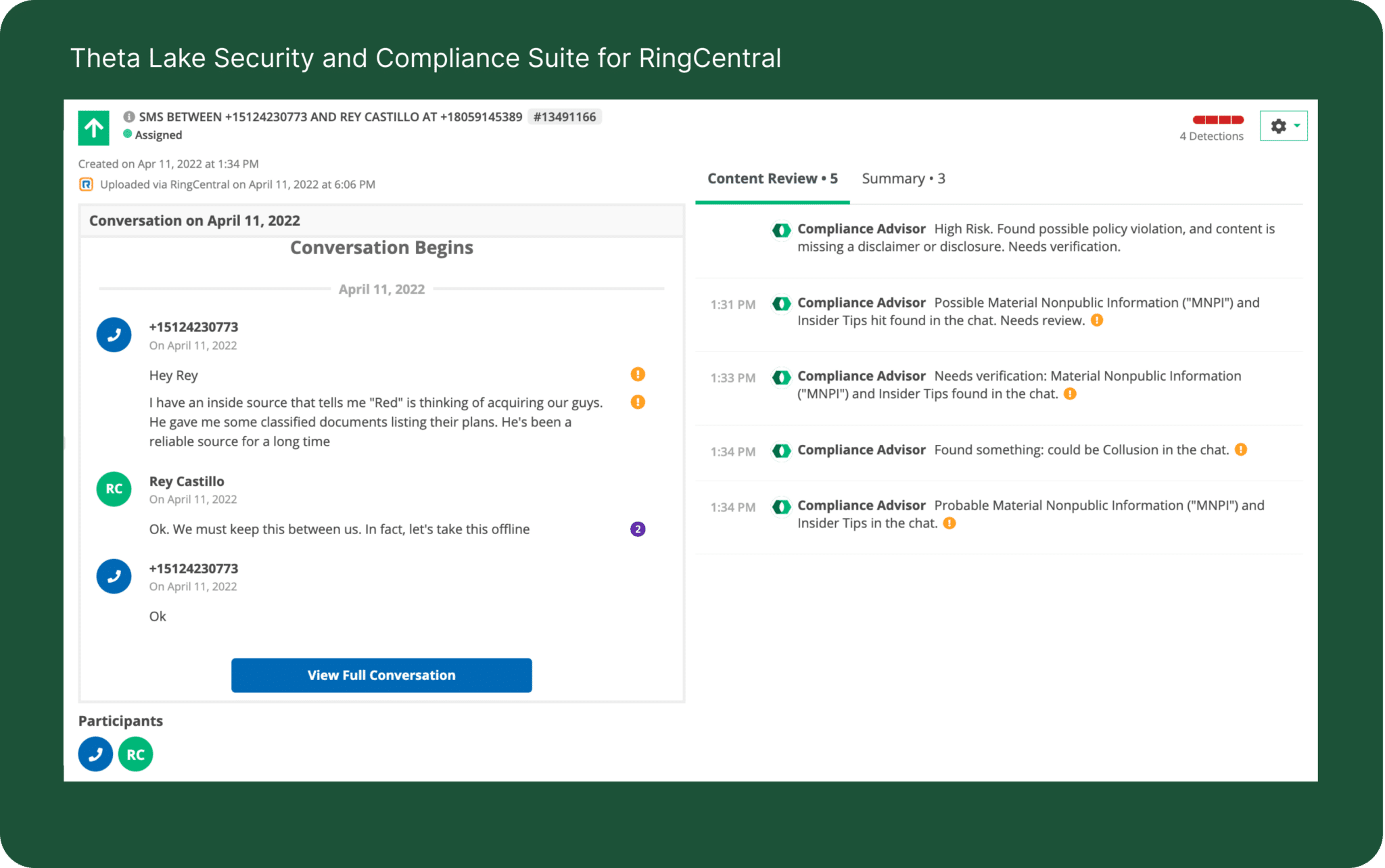
Our tightly-integrated solution with Theta Lake not only provides compliant archiving across all media types, but also enables the detection of compliance conduct risks and sensitive data exposure risks.
Theta Lake helps organizations meet content capture and supervision requirements for voice, chat, and video calls using RingCentral, and gives IT and compliance teams deep security and compliance collaboration coverage needed for hybrid and work-from-anywhere environments.
Theta Lake provides integrated archiving, eDiscovery, legal-hold, data loss protection (DLP), and surveillance of all RingCentral communications, including RingCentral Video, Phone, SMS, messaging/chat, voicemails, and RingCentral Global Service Providers.
Securing your mobile workforce
Whether your teams are in-office, remote, or hybrid, keeping your data secure while they work from anywhere is our biggest priority. And these are just a few ways we help you safeguard your communications.
To learn more about our security posture, check out our security white paper below:
Updated Mar 13, 2025