End to End Encryption – Everything You Need to Know and More
In a world where business is increasingly carried out virtually, appropriate cybersecurity is vital. Having strong security protocols covers your business morally and legally should there be an issue. It also helps build trust with clients and customers, as well as among your staff.
Cryptography has advanced data security hugely in recent years. One of the best ways to keep your data secure in the workplace is to encrypt it. Encrypted data is data that’s been translated into code, usually a series of random characters, with an accompanying ‘key’ to decrypt it back into plaintext once it arrives at its endpoint.
End-to-end encryption is just one type of encryption security.
What is end-to-end encryption?
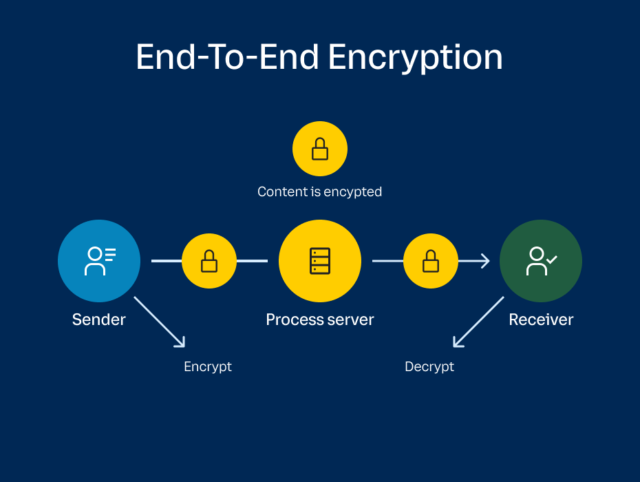
End-to-end encryption (E2EE) is an encryption method where the content of your message is visible only to the sender and receiver. The sender’s device encrypts the data using an encryption key, and only the intended recipient can decrypt it by using the decryption key.
End-to-end encryption vs other encryptions
E2EE is a thorough encryption method. It uses two keys to encrypt data: an encryption key and a decryption key. It’s also called ‘asymmetric encryption’ because different keys are used to encrypt and decrypt data.
Another type of encryption, known as secret key or symmetric encryption, uses only one key to code and decode data. This is simpler to use than E2EE but comes with a greater risk of corruption or interception of your data.
What does end-to-end encryption protect?
The goal of E2EE is to protect data from being read, leaked or lost. There are two major ways in which this usually occurs. E2E encryption stops both.
- Prying eyes. Only the sender and recipient can view encrypted messages after decryption, so E2EE keeps sensitive data out of view of anyone who doesn’t strictly need access to it. This type of encryption prevents hacks by stopping hackers from reading data even if it’s intercepted.
- Tampering. Without the keys, there’s also no way to change an encrypted message without the alteration being obvious. This is because the decryption key isn’t sent with the message; rather, the recipient already has it.
End-to-end encryption stops unintentional reading too. For example, in an open office environment, it’s possible to send a message containing sensitive data in error, which can constitute a serious breach of data protection laws. E2EE helps prevent this.
E2EE protects all of the data within the message but not the metadata.
How does end-to-end encryption work?
Encrypted messages use end points – ie the start and end of a message’s journey – to store their keys. This is called ‘public key encryption’.
The first key is stored at the point of sending and contains the code for encryption. The second is stored at the point of receipt and contains the code for decryption. In transit, your message appears as a series of random characters.
As a result, data cannot be read or altered by your service provider, any messaging apps or unintended recipients.
What services use end-to-end encryption?
Many service providers, such as those offering WiFi and mobile apps, have adopted end-to-end encryption to prevent data leaks and maintain customer satisfaction.
Apple devices that work on their iOS operating system, including Mac computers and the various iPhone models, use E2EE to send and store data kept in the cloud. For example, if you wish to access stored passwords on an Apple device, you must provide an authentication code or submit to facial identification.
Android devices offer E2EE security for text messages between users.
Individual service providers are also fans of E2EE’s enhanced security. For instance, Windows cloud storage, WhatsApp, Microsoft Teams, Telegram and Gmail all use it in their services in addition to security code requirements and passwords.
These services primarily use E2EE to keep customers safe. Mobile devices and cloud storage mean vast amounts of personal information is stored remotely. This includes banking details, names, dates of birth, and current locations. It’s important for services like Apple and Microsoft to keep this data secure and avoid any leaks.
The advantages of using end-to-end encryption
Of course, you’ll need to understand the advantages of E2EE before deciding if it’s a necessary step for your business. Most of the major benefits of it relate to increased security and data protection.
It keeps your data secure
With end-to-end encryption, you’re the only one with the private key needed to decrypt your data. This means you can store it safely without the risk of tampering or leaks. Only the intended recipient is able to read and edit this.
This is particularly important for businesses that handle flows of sensitive data that are legally protected. For example, client names and financial details are kept safe under the General Data Protection Regulation (GDPR).
E2EE also keeps personal devices secure. This is important in all areas of your life, but particularly if you use these for work. Any emails and text messages you send can be encrypted to avoid corruption, preventing friends and colleagues from receiving spam.
It keeps your data private
An integral feature of E2EE is encryption in transit. This means your data is encrypted if it’s intercepted at any time between being sent and received. While this isn’t a perfect strategy, it’s highly effective at preventing data leaks after interception.
If you use a communication services software like Google Suite, data is stored there and can be decrypted. If this happens, it’s no longer totally secure. However, with E2EE, your data is private wherever it’s kept.
Protects admins
Cyber attacks often target system administrators. Because admins don’t hold the decryption keys with end-to-end encryption, these attacks can’t leak useful data.
Data security is, in many cases, a legal requirement as well as business best practice. Therefore, staff responsible for data security accept potential legal implications in the case of a leak. For their sake, strong security should be part of your company culture.
E2EE is a great way to cover admins by ensuring the highest possible level of security online.
The disadvantages of end-to-end encryption
Most security features come with minor disadvantages. E2EE is still a very secure way of protecting data, but let’s look into a few of the potential downsides of this approach.
Too much privacy
The major argument against end-to-end encryption comes from the field of law enforcement. Law enforcement agencies often need to access sensitive data as part of their investigations. This can prove difficult because they don’t have the keys required to decrypt data without the receiver.
Some organisations have also expressed concerns that end-to-end encrypted data may allow users to share illicit or inappropriate materials because service providers can’t view what’s being sent.
Visible metadata
E2EE works to conceal data within a message. However, it doesn’t hide data about it.
This usually carries little risk, but it can be a problem if it shows when the message was sent and where it came from. A party with ill-intent may be able to deduce weak points in the encryption protocol, such as when they could insert malware into a message pre-encryption or after decryption.
Irrespective, E2EE is still one of the most secure ways to protect sensitive data.
Endpoint security
There are a few things that can make endpoint security a lower standard. Firstly, you need to define your endpoints carefully. If you don’t and the recipient is unclear, decryption is possible at certain points in the transmission process.
As with all forms of data sharing, you may also find physical security weaknesses at your endpoints. Endpoints should be out of view of the public and kept secret as far as possible.
Weak recipient security is one of the potential pitfalls of hybrid working. This is particularly true for staff using personal devices which they share with other family members. You should avoid this where possible if receiving or sending data that needs to be encrypted for security purposes.
Explaining the end-to-end encryption in the RingCentral Cloud Solution
Cloud-based communication solutions are exploding right now. This means businesses can store large quantities of data and easily send it between users.
Security can be a concern because data stored on the cloud is held in external servers. Luckily, RingCentral’s communication security features are designed to prevent leaks and hacks and give users peace of mind.
Some of the features of our end-to-end encryption include:
- Identity verification. At the endpoint, users are asked to verify their identity before accessing sensitive data to ensure data protection compliance.
- Encryption in transit. We protect your data when transferring it between endpoints to prevent hackers or unauthorised users from viewing encrypted information.
- Assigning permissions. Admins can assign security permissions to individual users, so only they can access appropriate information
- Personalised storage. You can download and delete your data as it suits to maintain privacy.
Protecting messages from tampering or leaks is essential to maintaining trust, and adding E2EE security to your messaging and calling system enables you to safeguard staff and customer data quickly and easily. You can even end-to-end encrypt your video calls to add an extra layer of security to sensitive meetings.
For further information on how RingCentral can provide communication services with high-quality security for your business, take a deep dive into our archives with this white paper on video security.
Originally published Apr 12, 2022