Security Operations: A Look at a Security Operations Centre (SOC)
A Security Operations Centre is an advanced security function that assumes responsibility for an organisation’s entire cybersecurity strategy.
As society grows more security-conscious and embraces the shift away from legacy systems to cloud integrations and virtual solutions, more businesses than ever are building virtual or hybrid security operation centres.
This article will take a look at the structure, functions, and tools of modern SOCs to demonstrate just how valuable they are to monitoring and improving an organisation’s security and incident detection and prevention.
What Is Security Operations (SecOps)?
As IT security grows more intricate by the day, it has become impractical for it to exist separately from IT operations. Security Operations (SecOps) establishes a seamless collaboration between an organisation’s IT security and IT operations team, integrating procedures, tools, and technology to prevent data silos.
Because both teams assume joint ownership and responsibility for security issues, they are empowered to operate in alignment with shared goals. This means that security is no longer an afterthought in IT operations, and IT security teams can implement processes without compromising IT performance.
What Is a Security Operations Centre (SOC)?
A Security Operations Centre (SOC) is a facility dedicated to the long-term monitoring and management of an enterprise’s security posture. The SOC team is responsible for preventing, identifying, analysing, and mitigating cyber threats on a 24/7 basis. Their defensive tactics are assisted by a wide range of technology solutions and governed by best practices.
How Does a Security Operations Centre Work?
To understand how a SOC team strives to perform preventative measures, incident response, and threat analysis, let’s take a look at a typical SOC’s strategy and infrastructure.
Strategy
The framework of a SOC strategy aligns with five core principles and use cases: security monitoring, analysis, incident response, auditing, and threat hunting. We can understand each stage of a SOC strategy in action better by observing the roles of the SOC team.

SOCs consist of security analysts, engineers, and other specialised personnel. The hierarchical approach that SOC teams adopt in their roles and responsibilities aligns with the above principles.
Tier 1 – These are your first-line incident responders. As well as administrative tasks like the configuration and management of security tools and systems, tier 1 analysts monitor, triage, and distribute threat alerts.
Tier 2 – Once a threat is received, second-line incident responders start a thorough analysis, investigating the nature of the attack, where the threat came from, and which parts of the IT infrastructure are affected. Armed with this information, they can remediate the threat appropriately.
Tier 3 – A tier 3 analyst performs auditing, vulnerability assessments, penetration testing, threat intelligence, and other duties to detect security risks and vulnerabilities within the network.
Tier 4 – At the top of the hierarchy sits the SOC manager. They have a wide range of responsibilities, including sourcing talent, designing strategies and best practices, managing resources, and overseeing processes while equipped with the expertise to assist in crises.
Infrastructure
It was once standard for SOCs to be physical, heavyweight structures stationed in high-security, centralised locations. Naturally, this was unsupportive of a SecOps mentality. However, many businesses are now adopting a virtual or hybrid SOC to maximise workflow and efficiency.
RingCentral’s cloud services are supported by a remote team of global cybersecurity experts operating in virtual SOCs.
Focus Areas and Benefits of SOC
Most SOCs attend to all of the below areas in their strategy. However, the specific focus areas and use cases of a SOC differ in their level of prioritisation depending on business size, industry, and their level of security maturity.
Control and Digital Forensics
This focus area is concerned with penetration and vulnerability testing. It prioritises the hardening of an organisation’s security posture, delving into the infrastructure to detect weaknesses and any evidence of malicious activity.
Monitoring and Risk Management
The observation, collection, analysis, and management of log events and security systems is a primary focus of most SOCs. SOC teams aim for complete visibility over networks, servers, endpoints, applications, and other systems to determine baselines and verify compliance.
Risk management procedures aim to gather a comprehensive overview of how current vulnerabilities or security incidents may impact an enterprise at an organisational level.

Security Incident Detection
Incident detection and response is fundamental to any SOC strategy. SOCs use a variety of tools, most notably a SIEM, for 24/7 incident detection. This decreases the gap between the time of compromise and the time of detection.
SOC Benefits
We’ve just established that the ability to respond to security threats quicker and with more accuracy is a standout benefit of SOC implementation. No matter the type of threat, where it originates, or the time of day it occurs, a SOC team can be on hand to mitigate the problem. Naturally, modern SOCs are also focused on protecting remote workers from cyber attacks as well as in-office workers.
And, of course, we all know that prevention is better than cure. With a SOC that focuses on penetration and vulnerability testing, and an up-to-date knowledge of cybersecurity trends, threat intelligence, and industry news, organisations are much better positioned to thwart attacks before they even have a chance to occur.
Network and System Administration
Alongside the focus areas above, many SOCs perform network and system administration. Not only does centralised administration allow for processes to be aligned accordingly, but these tasks play a fundamental role in the health and efficiency of the overall SOC. Such tasks might include:
-
- Firewall configuration and management
- Identity and access management (including meticulous password hygiene for network, software, and social media accounts)
- Endpoint management
- Allowlisting and denylisting
- Patch management

SOC Tools: Traditional Tools of SOC vs. Next-Gen Tools
SOC experts rely on an assortment of tools to implement their security processes. Let’s take a look at some traditional SOC tools vs. next-gen tools to get an idea of how modern SOCs offer advanced capabilities through the use of AI and machine learning.
Traditional SOC Tools
-
- Security Information and Event Management (SIEM) – commonly known as the ‘brain’ of security operations
- Vulnerability scanners and penetration tools
- Intrusion Detection System (IDS)
- Intrusion Prevention System (IPS)
- Firewalls or Next-Generation Firewalls (NGFW)
Next-Gen SOC Tools
-
- Next-Generation SIEM
- Network Traffic Analysis (NTA) tools – detects and monitors suspicious network behaviour
- Endpoint detection and response (EDR) tools – provides an efficient response to widespread attacks on endpoints
Traditional vs. Next-Gen SIEM
SIEM software is the SOC’s primary tool and plays a fundamental role in incident response practices. Both traditional and next-gen SIEMs collect and normalise data from across your entire network, analyse it against a statistical framework to identify potential cyber threats, and aggregate the data for human accessibility to provide easily-interpretable and comprehensive alerts.
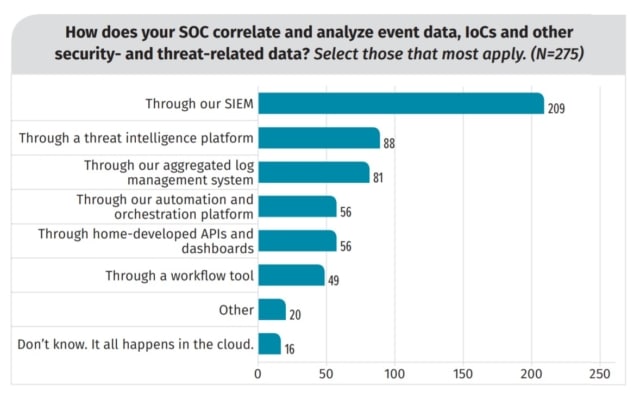
Next-gen SIEM service providers enhance these functions in the following ways:
Contextual enrichment: Aims to minimise white noise and increase time-to-response by enriching data insights. Where analysts would normally have to gather contextual information manually, a next-gen SIEM can provide an IP address, geolocation, asset ownership, peer grouping, and more.
Big data architecture: Next-gen SIEMs move away from proprietary security architecture and embrace big-data platforms. They are designed to handle huge volumes of data and support data retention, scaling, and advanced data science algorithms.
Enhanced behaviour analytics: A next-gen SIEM establishes accurate baselines by leveraging machine learning and statistical algorithms. This is known as User and Entity Behaviour Analytics (UEBA).
Automation: Incident response automation capabilities can be performed in alignment with playbooks ruling industry best practices. Workflow automation is also a possibility.
Cloud deployment: As most businesses migrate to the cloud, cloud-native SIEMs like the popular Microsoft Sentinel have paved the way for more visibility and agency than ever before. Cloud SIEMs allow for faster deployment times, cheaper implementation, and increased visibility over both on-premise and cloud infrastructure.
Functions Performed by the SOC
We’ve established that a SOC’s primary responsibilities are to monitor, analyse, and respond to security incidents, as well perform preventative measures. Let’s take a look at the primary functions of a SOC team in action.
Take Stock of Available Resources
One of the SOC’s first and most important goals is to gain complete visibility over an organisation’s threat landscape. This involves sourcing every single endpoint, server, and software in their IT infrastructure, both within on-premise data centres and in the cloud, as well as any traffic flowing between them. Full visibility is critical because even just one asset left unaccounted for is a potential access point for cyberattacks.
To develop a comprehensive plan and optimise workflow, the SOCs resource management strategy also accounts for the tools, software, finances, and skill sets available to it.
Preparation and Preventative Maintenance
A fundamental principle of security operations is that preventative measures are more efficient than rapid responses.
Preparation: The SOC’s aim is to stay one step ahead of cyberattackers. They provide security and threat intelligence, keep up-to-date with the latest cybersecurity innovations and trends, and meticulously monitor threat methodologies and developments to preemptively harden their systems and strategies against the threats of tomorrow.
Preventative maintenance: Outdated systems and unexpected failures can have disastrous information security consequences. SOCs routinely update systems, security policies, firewalls, software, and applications, along with the regular analysis and patching of vulnerabilities.
Continuous Proactive Monitoring and Compliance Management
Proactive monitoring: Monitoring tools perform automated 24/7 scanning of the network, notifying the SOC in real-time of any suspicious activity or imminent threats. Next-gen SIEMs perform behavioural analysis to establish baselines for ‘normal’ behaviour and flag any abnormal patterns, as well as triaging threats for urgency.
Compliance management: The SOC must regularly audit their processes to verify that they comply with benchmarks set by governing bodies or industry regulations.
RingCentral is GDPR compliant as per the legal requirements in the UK. This is simply to ensure the protection of sensitive data and reduce the risk of financial or reputation-damaging security breaches. Other regulations include HIPAA and PCI DSS.
Alert Ranking and Management
While automation tools are used to accelerate the process of triaging threats, it is the SOC team’s responsibility to analyse each alert thoroughly to assess the attack’s nature, origination, and urgency.
Threat Response, Security Refinement, and Improvement
Threat response: The SOC responds to threats with defensive tactics designed to cause minimal damage or downtime to business operations. Responses might include deleting infected files, terminating processes, and isolating or aborting compromised systems or endpoints.
Security refinement: There are a few procedures that SOCs follow after responding to a threat, one of these being security refinement. The success of the response – or lack thereof – can provide data-driven insights that improve the accuracy of a security roadmap as well as current processes.
Recovery Remediation and Root Cause Investigation
Two other procedures that follow a threat response are:
Recovery remediation: After a threat is successfully managed, the SOC will attempt to restore system operations and perform recovery verification. This process will vary in complexity depending on the nature and severity of the attack: it could be as simple as deploying backups to evade ransomware or as complex as reconfiguring entire systems that were infected with malware.
Root cause investigation: SOC teams will scrutinise log data to determine exactly where and how the threat occurred. This maximises security refinement efforts and helps to verify that any threats have been successfully eradicated.
Log Management
Effective log management practices are crucial to visibility. Log management involves the collection, maintenance, review, and analysis of network activity data. This comprehensive data is used for everything from establishing baselines, identifying abnormal behaviour, assisting in root cause investigations, highlighting areas for process improvement, and more.
Challenges When Building Security Operations Centre
In a 2019 study, it was discovered that while lots of organisations were migrating to the cloud, plenty were still using centralised systems. The study deemed this “problematic” due to “data protection laws and regional variation of requirements, as well as tactical understanding of the systems in use”.
IMAGE HERE
Other prevailing challenges of a traditional SOC include:
Limited Visibility
There are limitations and restrictions to what an internal SOC can access. Anything outside of the organisation’s internal infrastructure, like third-party servers, tools, or encrypted data, may present blindspots.
White Noise
The volume of data that SOCs handle is astronomical, and teams can quickly become so inundated that filtering out the white noise turns into a stressful, time-consuming task. Next-gen SIEMS use machine learning, automation, and analytics to distinguish security data from non-security-related data to mitigate this issue.
False Positive and Alert Fatigue
False positives happen when security systems send mislabeled security alerts, resulting in the SOC wasting time and resources on inspection and analysis. Too many false positives can distract the team away from legitimate alerts and make them harder to spot.
The Security Operations Controls at RingCentral
RingCentral is dedicated to protecting all of your information with seven layers of enterprise-level security. Equipped with a global team of cybersecurity experts, government-compliant data centres, and regulatory best practices built into every policy and operational process, RingCentral’s products are designed to provide all the security services to fit the needs of security mature enterprises.
With RingCentral, you’re promised the following IT security operation controls:
- Identity and access management
- Network security
- Application security
- Vulnerability management
- Threat detections and mitigations
- Patch management
- Data encryption
Originally published Dec 22, 2021

