What is an Endpoint?: Vital Components, Strategies and Benefits
Data breach costs have risen by 12.7% in the past year since 2020. This is at an all-time high.
As more people work from home and on the go, it’s become increasingly important to secure the devices you use from endpoint threats, like malicious cyberattacks and data breaches. In this article, we’re going to go over precisely what endpoints are, why they’re essential, and what you can do to protect them.
Embracing today’s technology to mobilise a remote workforce shouldn’t be hampered by security concerns and bad actors. RingCentral MVP can provide everything you need to organise your remote team, improve your system’s user experience, streamline your workflows, and, crucially, give you peace of mind with powerful security monitored around the clock.
What is an endpoint?
Endpoints are any end-user devices connected to your network. Many of the devices you use every day at home and while working are endpoints. Here are a few examples:
- Laptops
- Mobile devices
- Tablets
- Printers
- Smartwatches
As Bring Your Own Device (BYOD) policies and the Internet of Things (IoT) become increasingly popular, the number of connected devices on one network can reach hundreds. That’s a lot of endpoints and a lot of potential security risks.
Here’s a look at how IoT devices are expected to grow in the next decade:
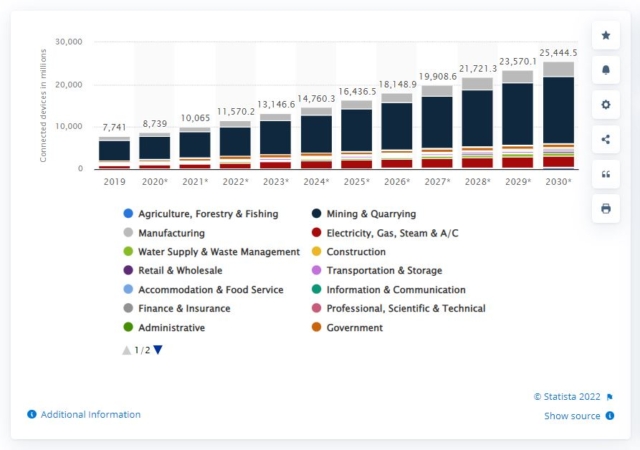
As more and more endpoints enter the market, ensuring their security will continue to be a priority.
Another critical aspect of endpoints is API endpoints. APIs (Application Programming Interface) allow two systems to interact and communicate with each other. When two systems communicate, the points of entry to the communication channel are the API endpoints.
Businesses use APIs to share essential information, processes, and transactions, and their use is only becoming more prevalent. Securing API endpoints is an additional consideration to remember when choosing your security solution.
What is endpoint security?
If your house were an endpoint, the endpoint security would be the lock you put on the door. Anyone could get in if you didn’t have a lock on your door. Endpoint security acts as the lock for your endpoint; it prevents cybercrime.
Cybercriminals look for weak endpoints as entry and exit points to access information on an organisation’s network. Once they’ve obtained information through the endpoint, they hold the data hostage for ransom or to cause disruption.
Endpoint security protects all your endpoints—smartwatches, API endpoints, printers, IoT devices, you name it—from cybercriminals looking to exploit vulnerable devices. While traditional security services like antivirus software, email and web filtering, and firewalls used to be enough, today’s sophisticated programs need more robust security and threat detection.
RingCentral provides a secure and reliable communication system for your business operation with several layers of built-in security at every level of our architecture and processes.
Our security measures include the physical, network, host, data, application and business processes, as well as the enterprise level of your organisation. These measures ensure that critical systems, intellectual property, and customer and employee data are protected from ransomware, phishing, malware, and other cyberattacks.
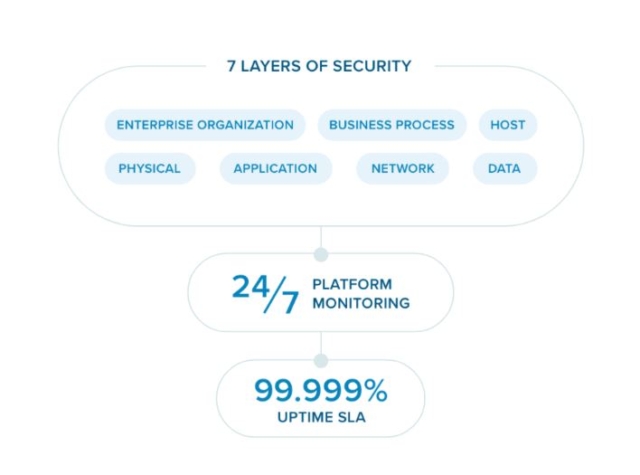
How does endpoint security work?
Cyberattacks have become more sophisticated as technology has advanced, but measures to protect against cyberattacks have also adapted. It’s just a matter of implementing these security measures into your system.
The chart below illustrates the increase in threats, endpoint risk, and the lacklustre protection traditional antivirus software provides.

One type of security feature, Endpoint Protection Platforms (EPP), looks at files as they enter your network. The EPP works through a centralised dashboard installed on a network gateway or server that allows administrators to control each device’s security remotely.
The client software is assigned to each endpoint as SaaS that can either be managed remotely or installed directly on a device. This can push updates, authenticate log-in attempts, and execute corporate policies by using application control and encryption, EPPs secure endpoints.
Some EPPs use Endpoint Detection and Response (EDR). EDRs can detect more advanced threats, like file-less malware and zero-day attacks. With continuous monitoring, the EDR system utilises better visibility, offering a variety of response options.
Benefits of endpoint security
Unfortunately, many of the devices we use at home and work are subject to threats from cybercriminals, like ransomware. Having a multi-layered security approach that includes endpoint security can keep your devices safe.
Endpoint security products protect your devices from traditional malware, file-based and file-less threats, and macro attacks. With your devices protected, you don’t need to worry about spending money on the remediation of malware-related issues, and your IT team will be free to place their focus elsewhere.
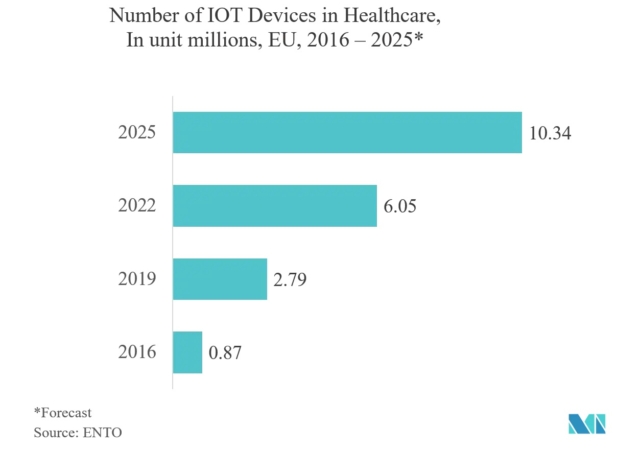
Depending on your industry, an endpoint security service may be non-negotiable. Industries that handle sensitive information, like healthcare, finance and retail, must adhere to data security regulations, which require a robust security plan that includes endpoint security.
This is especially important as endpoints increase in certain sectors. The chart below shows the significant increase in IoT devices in healthcare in recent years.
Endpoint security components
So what does endpoint security entail? Here are some of the components that make endpoint security valuable:
- Zero-day threats can be detected in real-time with the help of machine learning and automation.
- Protection from malware on multiple endpoints.
- Web security to protect web browsing.
- Firewall integrations.
- Email protections to prevent phishing attempts.
- Threat reports and analytics so administrators can identify problems quickly.
- Extended detection and response (XDR) collects and correlates data across multiple security layers.
Endpoint security vs endpoint protection
Although there’s some confusion around the differences between the terms endpoint security and endpoint protection, these refer to the same security tools that protect networks against security threats.
Endpoint security vs firewalls
Firewalls and endpoint security are similar in that they both provide security from cyber threats. However, how they provide protection is very different. A firewall is a gateway that filters network traffic—it’s a type of network security.
There are two types of firewalls. Host-based firewalls run on host computers, and they monitor traffic going in and out of those specific machines. The other kind of firewalls, network firewalls, filter traffic between two networks, like the internet and a business’s network.
Endpoint solutions might have firewalls as a part of their bundle of features, but a firewall on its own isn’t enough for the amount of data processed today. For a layered security plan, organisations should incorporate both methods of security.
Endpoint security vs network security
While endpoint security protects vulnerable endpoints like computers, mobile phones, IoT devices, etc., network security runs on a network layer and protects the network. Endpoint devices can then connect to the network.
Endpoint security strategies
When you have a lot on your plate, like planning a product launch webinar, the last thing you want to worry about is the security of your endpoint devices. RingCentral provides a multi-layered, powerful security solution that protects your devices on all levels.
Transport Layer Security (TLS) and Secure Real-Time Transport Protocol (SRTP) encryption between all endpoints mean all your business calls are safe with RingCentral. You can also count on the following:
- Firewalls and session border controllers for your networks and applications.
- Multiple authentication levels for administrators.
- Intrusion-detection systems and fraud analytics to protect your businesses’ technology.
- Monitoring of operational functions with vulnerability scans and system hardening.
With this layered approach, all of your technological weak points are covered and monitored.
RingCentral’s platform extends across SSAE 18 and ISO 27001-audited data centres, protected by electronic prevention systems, on-site engineering specialists, and security guards. Locations are spread out across diverse geographic regions to minimise service interruption and limit the risk of catastrophic data loss.
RingCentral has your back regarding computer security threats, but we also protect your business from toll fraud. Toll fraud is the unauthorised use of your phone service, equipment, or phone lines to make long-distance calls. Our global security department actively monitors your account to detect irregular calling patterns and prevent fraudulent charges.
RingCentral also provides regulatory implementation to cover all kinds of scenarios. For example:
FINRA: To assist FINRA-regulated customers, RingCentral uses applicable cybersecurity requirements from SEC regulations. All RingCentral call recordings, call logs, fax exchanges, SMS, MMS, audio and web conferencing, and team messaging communications comply with relevant SEC regulations.
HIPAA: To meet HIPAA security requirements, RingCentral has implemented HIPAA security safeguards. An annual third-party SOC 2+ audit is performed, including an assessment of controls mapped to the HIPAA Security Rule requirements that shows the implementation of the security measures and conditions outlined in the HIPAA Security Rule.
On top of all that, RingCentral MVP has obtained Skyhigh’s CloudTrust rating of Enterprise-Ready, which also happens to be its highest rating possible. Skyhigh awards this status to cloud services that meet strict standards for data protection, identity verification, service security, business practices, and legal protection.
CTA: Adopting an endpoint security solution doesn’t have to be a hassle. By researching and investing in the right security solution, you’ll be able to keep your business running safely wherever your team is working.
Don’t risk any more of your time and money with outdated security software that leaves you vulnerable. Check out how RingCentral can support your security efforts here.
Originally published Oct 18, 2022

