Starting a new business is an exciting time in an entrepreneur’s life. Your plans and dreams begin to materialize, and the only limitation is your imagination. And with the incredible opportunities of the internet, you can reach audiences, customers, and clients from around the world.
But—and you knew there was a “but” coming—the internet also leaves your small business open for potential cyber threats. As a startup, communication and collaboration are key to your growth from day one, and it’s likely these important conversations happen mostly online. So how can you make sure your big ideas aren’t vulnerable?
You’ve read about meetings getting taken over and vital data becoming compromised, but you’re not really sure what you can do to protect your new business. Or if it’s even right for you.
In this article, we’ll cover everything you need to get started with protecting your startup:
- Why should I care about cybersecurity for my startup?
- Why would cybercriminals want to go after my business?
- What are the most common types of cyberattacks?
- 6 best practices to secure your startup
👀 What are the 4 key components of a successful startup?
Why should I care about cybersecurity for my startup?
Cybersecurity is important for any business—whether you’re a startup or a multi-billion dollar corporation. Every aspect of your business is vital to making sure it runs smoothly, and a data breach or compromise can lead to catastrophic results.
The first reason is because you care about your new business, so why not protect it? A common misconception about a cyberattack is that it’ll never happen to you—until it does. According to this 2019 Hiscox Cyber Readiness Report, nearly 65% of all businesses have experienced a cyber-related issue. And of those businesses, 60% of businesses targeted by cybercriminals go bust within six months.
Another reason is a cyberattack costs a lot. Like a lot, a lot. From that same report, the average cost of a cyberattack for a business is $200,000 a year. Think of what your startup can do with $200,000!
On top of that, according to Security Intelligence’s 2020 Cost of a Data Breach Report, it takes an average of 280 days to identify and contain a data breach. And for those companies that have shifted to a remote work model, 76% of surveyors anticipate even longer response times for identifying and containing a data breach. So not only will it cost a lot, it’ll take a significant amount of time away from growing your business.
And the last reason is trust. If you work with customers, having any kind of data leak can absolutely destroy a company’s reputation. According to Ping Identity’s 2019 Consumer Survey: Trust and Accountability in the Era of Data Misuse, 81% of people would stop engaging with a company in any capacity if they had a data breach. As a brand new company, this time is crucial to building trust with the customers who are taking a chance on you.
Basically, skimping out on your new business’s cybersecurity is never, ever worth it.
Why would cybercriminals want to go after my business?
Maybe you’re not convinced. You’re a new business, you’re still small, so hackers aren’t going after you… right?
Unfortunately, small businesses and startups are a perfect target for cybercrimes. When you’re just starting out, you might not think there’s a security risk, or you may have a team that doesn’t understand the importance of cybersecurity. Hackers recognize and exploit these vulnerabilities, so they can take advantage of your business.
And you may think that just because your business doesn’t handle medical or financial data, you’ll be alright. That doesn’t matter to a hacker—every kind and size of business is an opportunity:
Ideas and intellectual property
If you’re working on the next big innovation, all of your hard work, countless prototypes, and drafts will have been for nothing if it gets into the hands of someone else.
Customer data
If your business provides a service for a customer, you’re probably handling some potentially sensitive personal data like their email address, home address, social security number, credit card information, employee names and information, and more.
Clients, partners, and investors
They might not even be after your or your customer’s information—they could want your client list and any associated information to target bigger companies with more valuable data.
Okay, okay, you might have some information a cybercriminal wants, but how can they get this data in the first place?
What are the most common types of cyberattacks?
There are countless ways your data can be targeted, but the most common methods are:
Phishing
If you’ve ever received an email with a suspicious link or a weird attachment, that’s phishing. Everyone gets these kinds of emails, and they’re relatively easy to identify. But as the internet gets more sophisticated, so do the phishing attempts. These links or attachments usually cause malware to be downloaded to a user’s device.
Ransomware
Ransomware is when a user installs a software onto their device—usually by being tricked into thinking it’s needed to scan their computer for viruses or something similar—and that software locks the user’s screen or their entire device and holds it ransom. The user won’t be able to access anything until they pay a fee to some random person before their system can work again. The victim won’t be able to access anything until they pay a “fee” to the attacker. Otherwise, they’ll remain locked out of their system. According to a recent industry study by Programs.com, nearly 7 out of 10 companies have experienced a ransomware attack caused by similar deceptive downloads, where users unknowingly install malicious software disguised as legitimate tools.
Data breaches
We’ve already talked about this a few times already, but a data breach is when secure or confidential information is exposed. Sometimes, this can happen by accident, such as a misdirected email, or intentionally by an untrusted source, like hacking.
6 best practices to secure your startup
Now that you understand how serious a cyberattack can be, you’re ready to take some steps to secure your startup. Many of our suggestions are perfect for getting started, and there are even more steps you can take to secure your startup. Of course, this all depends on how much you decide to budget for your business’s security and where you’re at in your business’s lifespan.
1. Assign an account admin and role-based users
If you have a small team, it may seem like granting admin access to everyone will communicate transparency and allow them to download the programs they need to do their job most efficiently. This can, however, leave any (and all) data vulnerable to cyberattacks. It’s best to assign one (or a few, depending on your team) person to manage access to data like customer info, employee info, financial records, and whatever else you don’t want the wrong person to see.
You should also set up user roles. This will allow you to set specific permissions per person or team. For example, if your accounting team needs to see financial records, but your marketing team doesn’t, you can set those parameters easily without creating one blanket user permission.
2. Strong passwords
Weak passwords are one of the easiest ways for hackers to gain access to sensitive information. Your passwords should always be complex and unique with a mix of numbers, letters, and symbols. There are a bunch of great password managers, like 1Password, Psono, or Dashlane, that are incredibly secure, suggest complex passwords, and even alert you if a login is compromised or if your email has shown up on a data leak. Many also integrate directly with your browser or operating system.
3. Secure apps and software
One of the most basic methods of securing your startup is to make sure all of your apps and software are up to date with current security enhancements. Old software with outdated security measures can be more at risk for a cyberattack, due to unresolved vulnerabilities. If you’re using software or an app that is no longer supported, it is really time to look for something newer and consistently updated.
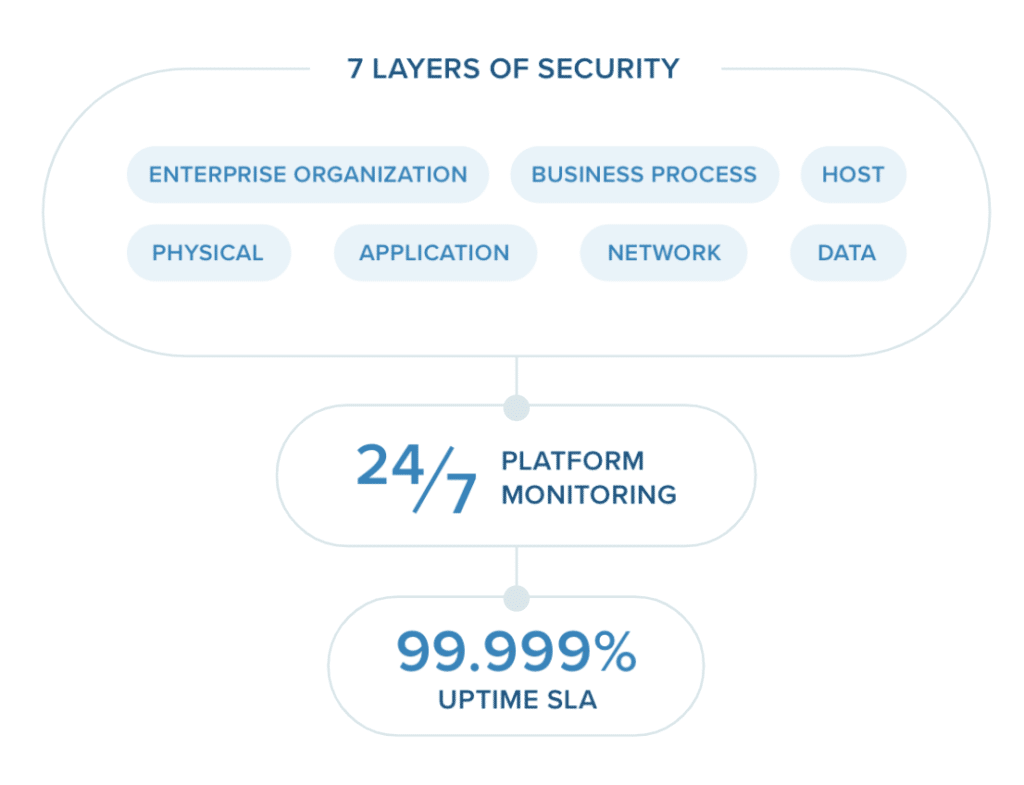
Simplifying to a single, unified app for your messaging, video, and phone in one secure platform ensures all of your communications are held to the same level of security. It also cuts down on the need to toggle between apps and worry about security updates for each separate application. For example, RingCentral’s cloud communications app handles all of your communications with seven layers of security to ensure you’re protected from attacks:
4. Multi-factor authentication and Single Sign-on
Thankfully, multi-factor authentication is becoming more and more common. Instead of relying on only a password, you can employ multi-factor authentication as an additional step to log into an account. Typically, this is done using an authenticator app, like Authy or Okta, which sends a push notification to the owner of the account to confirm that it was them trying to log in.
Some providers also do this in combination with a Single Sign-on feature that allows a user to use one set of login credentials to access multiple applications.
5. Firewall
Establishing a firewall is essential to protect yourself against cyberattacks. Your firewall acts as a barrier around your network, monitoring incoming and outgoing traffic and blocking malicious data packets and external threats.
6. Make security part of your culture
Last, and certainly not least, you should instill a work culture that prioritizes security. You should communicate with your team the steps they need to take to keep their, the business’s, and clients’ information safe. That means training your employees and your management team on new guidelines or principles for handling sensitive data. It’s also just as important to introduce your employees with robust personal security mesures, such as identity theft protection services.
🔍 Get this free eBook to learn the 4 key components of a successful startup.
Cybersecurity for your startup
Hopefully, you’ve found this information helpful for keeping your startup safe from cyberattacks. By taking the time to learn even these basics shows that you’re serious about cybersecurity and ready to take the next steps to protect your business.
To learn more about how RingCentral can help your startup stay secure and successful, check out RingCentral for Startups.
Updated Oct 22, 2025