Security breaches have become increasingly prevalent in all industries. And, they pose serious risks to businesses.
These breaches occur when hackers gain unauthorised access to sensitive information. These may include customer data, intellectual property or financial data.
The media often highlights such incidents, leading to negative publicity, especially if customers’ personal information is compromised. This erodes customers’ trust in the brand, impacting its overall value.
You can protect your customer data by adding a digital certificate to your website. There are several types of SSL Certificates on the market, which can help you protect your sensitive data from hackers.
And numbers don’t lie. Security breaches have dealt significant blows to brand value in recent times. A recent study revealed that 74% of consumers become less likely to trust a company after a data breach.
The damage can be long-lasting, with 36% of customers stating they would lose trust in doing business with a breached brand altogether. Notably, stock prices of affected companies experience an average decline of 7.27% in just fewer than three weeks following major breaches. Failing to prioritise security can lead to severe consequences, underscoring the critical need for robust measures to protect brand value.
What is a Security Breach?
A security breach can be defined as an unauthorised access, exposure, or theft of a company’s sensitive information from digital systems. Such breaches can severely damage a brand’s value.
This is especially true if the value was built on trust and positive customer experiences. Your brand may suffer a loss of credibility if propriety information or sensitive customer data lands in the wrong hands.
A data breach can also adversely impact customer loyalty, and, ultimately, revenue. Brand value is intrinsically tied to a company’s reputation.
So, just a single security breach can tarnish that reputation, affecting the brand’s standing in the market. Here are four key reasons why security breaches mostly occur;
- Weak Passwords: Many security breaches result from employees or users employing weak passwords that are easy to guess. For example, using “password123” or “123456” as passwords opens the door to hackers. A breach caused by weak passwords reflects poorly on the brand’s commitment to safeguarding customer data. It raises questions about the company’s security protocols and can lead to public backlash, damaging the brand’s image.
- Lack of Employee Training: Human error is a significant contributor to security breaches. 74% of all data breaches are due to human error. Employees might fall prey to phishing scams, inadvertently downloading malware, or mishandling sensitive data. Without employee awareness and proper training on cybersecurity best practices, employees can unknowingly open the door to attackers.
- Unpatched Software: Failing to update and patch software regularly leaves systems vulnerable to exploits. For instance, a company may overlook updating its server software, leaving it susceptible to known security vulnerabilities. If hackers exploit such weaknesses and gain access to customer data, the brand faces accusations of negligence and incompetence, further eroding customer trust.
- Phishing Attacks: Cybercriminals often use phishing emails to trick employees into revealing sensitive information or granting access to secure systems. One employee falling prey to a phishing scam can result in a massive data breach. Customers may perceive such breaches as a sign of the brand’s inadequate employee training or lack of robust security protocols, leading to a loss of faith in the brand.
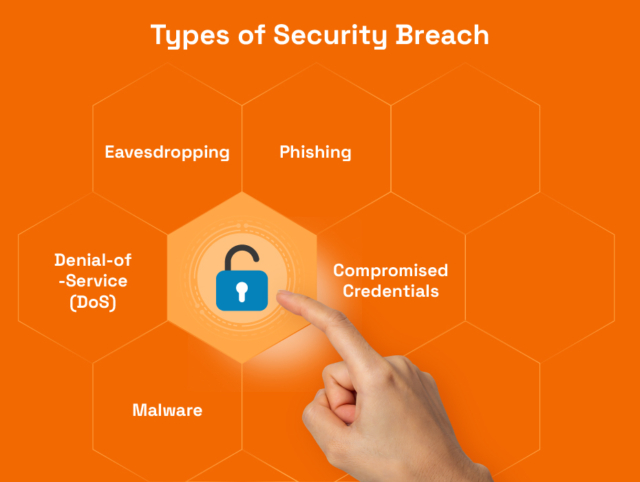
Different Types of Security Breach
Dealing with data breaches is an intricate challenge for many businesses. This is because these breaches can take various forms, infiltrating organizations through unexpected channels. Below are few types of security breaches;
- Compromised Credentials: This type of breach occurs when unauthorised parties gain access to sensitive accounts or login information. It can happen through various means. For example, an attacker may choose phishing or social engineering attacks. Once attackers have acquired valid credentials, they can impersonate legitimate users. Successfully executed, criminals can access confidential data and cause widespread damage.
- Phishing: Phishing is a deceitful tactic used by cybercriminals to trick individuals into revealing personal information, such as passwords or credit card details, through deceptive emails, messages, or websites. These fraudulent communications often appear genuine, luring victims into divulging sensitive data unknowingly. And phishing attacks can target anyone. From employees to customers, and even top-level executives, no one is safe. This is what makes phishing a prevalent and effective method for data breaches.
- Eavesdropping: Eavesdropping, also known as snooping or sniffing, involves attackers intercepting network communications to obtain sensitive data. Without encryption, cybercriminals can exploit unsecured networks or vulnerable connections to capture and analyse data packets. This allows them to intercept messages or extract valuable information like login credentials or personal data.
- Denial-of-Service (DoS): A DoS attack aims to disrupt the normal functioning of a website, server, or network, making it inaccessible to legitimate users. Attackers overwhelm the target system with an influx of traffic. This may make the target system crash or just become unresponsive. Now, a DoS attack doesn’t necessarily steal data. However, it can cause significant financial losses, reputational damage, and divert IT resources away from other critical security matters.
- Malware: Malware is malicious software designed to infiltrate systems and perform harmful actions, including data theft. This category includes;
- Viruses
- Ransomware
- Spyware, and
- Trojan horses
If installed successfully on a system, malware can give attackers unauthorised access to sensitive data. They can enable remote control, or files encrypted for ransom.
The Cost of a Security Breach
In 2023, the cost of a data breach soared to a staggering USD 4.45 million on a global scale, representing a worrisome 15% surge in just three years. This alarming escalation has left companies reeling and contemplating their cybersecurity strategies.
The repercussions of a security breach can unleash a devastating domino effect on businesses, leaving no stone unturned. It can impact various critical aspects of their operations, leading to;
- Loss of Revenue: Apart from the immediate costs associated with investigating and mitigating the breach, businesses may also experience a decline in sales and revenue. This can be largely due to the erosion of customer confidence. With compromised data and disrupted services, customers might hesitate to engage with the company. This may lead to decreased transactions and ultimately affect the bottom line.
- Reduced Trust (Client, Partner, Employee, and Vendor): A breach undermines trust at multiple levels. Clients and partners may lose faith in the organization’s ability to protect their sensitive information. This may lead to strained relationships and potential contract terminations. Employees might also become apprehensive about the security of their personal data. So, they may begin to question the company’s commitment to safeguarding their information. Also, vendors might reconsider their partnerships with the breached organization, leading to further challenges in maintaining business relationships.
- Customer Loss: Customer loyalty is fragile, and a security breach can shatter it completely. Customers who fall victim to data theft or other cyber-related issues may feel betrayed and abandoned, causing them to sever ties with the company permanently. Losing customers not only impacts short-term revenues. It also diminishes the potential for repeat business and positive word-of-mouth recommendations.
- Online Sabotage: Hackers may exploit a security breach to sabotage a company’s online presence. This could involve defacing websites, spreading false information, or disrupting online services. Such malicious activities tarnish the company’s digital image, causing harm to its reputation and deterring potential customers from engaging with the brand.
- Negative Effect on Customer Trust and Spending: When customers lose faith in a business’s security measures, they become wary of sharing personal information and conducting transactions online. This hesitancy can lead to reduced online spending and hinder the company’s ability to effectively tap into the digital market. As customers seek more secure alternatives, the business may struggle to regain their trust and lost opportunities.
- Damage to the Brand’s Name (Reputational Damage): Reputation is a vital intangible asset for any business, and a security breach can leave a lasting stain on the brand’s name. News of the breach spreads quickly through media and social channels. This does not only attract negative publicity but also public scrutiny. Rebuilding a tarnished reputation requires significant effort, resources, and time. This makes it challenging for many companies to restore their images in the eyes of stakeholders and the general public.
Fair to say, Large-scale security breaches have dealt devastating blows to several prominent brands and organizations, leaving indelible marks on their reputation, customer trust, and financial standing. Here are some of the most recent examples of significant security breaches and their far-reaching impacts:
- Nova Scotia’s Healthcare Sector Data Breach (June 2023): In a breach linked to Progress Software’s MOVEit application, data from over 100,000 employees was stolen, including sensitive details like Social Insurance numbers, addresses, and banking information. The province was using MOVEit for payroll transfers. The culprits, the Clop ransomware gang, also known as Lace Tempest, claimed responsibility.
- Leytonstone School Attack (June 2023): Leytonstone School in Waltham Forest was shut down due to a damaging cyberattack that compromised significant personal data. The attack, leading to a “critical IT incident,” prompted the closure of all year groups except GCSE students. The breach impacted the school’s IT systems, including Wifi and phones. Critical staff data was also left inaccessible due to the attack.
- The University of Manchester Cyber Attack (June 2023): In the week starting June 6, 2023, the University of Manchester fell victim to a cyberattack. It was confirmed that certain systems were breached by a criminal entity, resulting in the copying of a portion of data related to students and alumni. The University promptly notified those potentially affected and also took comprehensive measures to address the situation, including internal and external assistance.
Signs to Identify Security Breach (Early Warning Signs)
Detecting early warning signs of a potential security breach is crucial to safeguarding sensitive information and mitigating potential damage. Here are five key indicators to remain vigilant about:
- Unusual Activity: Keep a watchful eye on any abnormal patterns in system access, such as multiple failed login attempts, login from unusual locations, or after-hours access. Unusual data transfers, large downloads, or irregular data access by employees could also be red flags signalling a breach.
- Signs of Tampering: Look for signs of data manipulation or unauthorised changes in files, databases, or critical system settings. Any suspicious alterations, especially in high-security areas, can indicate unauthorised access or tampering attempts.
- Changes in Settings: Regularly review and monitor your system settings. Sudden alterations in firewall configurations, user privileges, or security policies can be indicative of an intruder trying to gain unauthorised access or compromise the system.
- Locked Accounts: Frequent incidents of locked accounts or sudden changes in user privileges without legitimate reasons could signify attempts to gain unauthorised access. It’s essential to investigate the root cause promptly.
- Device and Network Problems: Unexplained issues with devices, such as frequent crashes, slow performance, or unexpected behaviour, could be signs of malware or intrusion. Additionally, unusual network traffic patterns, unexpected network connections, or unexpected firewall alerts should raise concerns.
How to Protect Your Brand from Security Breach?
Cyber threats are ever-evolving, making it crucial for businesses–including those that have adopted remote work to adopt robust security measures. Here are some effective strategies to safeguard your brand’s integrity and customer trust;
Originally published Sep 06, 2023, updated Sep 11, 2023