The cost of a single data breach has significantly increased in recent years. In 2021, that cost reached an average total of $5.91M. Likewise, according to the IBM Cost of Data Breach report 2021, successful vishing or smishing attacks cost victims $317B that year.
This growing risk, plus the General Data Protection Regulation (GDPR) and its increasing fines, shows why it’s essential to scrutinise your vendor’s data privacy processes. In Q3 of 2021 alone, business fines totalled more than $1.6B. You could be at risk if you’re unfortunate enough to choose a UCaaS partner with a lax approach to security.
But finding a UCaaS provider with a bulletproof approach isn’t straightforward. It means knowing exactly what to look out for.
Let’s take a look at some tips you can follow when you’re considering what provider to go for.
Three things for your UCaaS security checklist
Transparency is key when it comes to finding a vendor with a responsible approach to their security practices. Your chosen vendor should be upfront about the investments and commitments they’ve made to safeguard your users and data. But it’s super important to know what you’re looking for when it comes to your vendor’s security pledge. We’ve outlined three non-negotiables to help you protect your brand and bottom line (more of these tips in the full guide).
1. Information security infrastructure
As the potential attack surface for cybercrime continues to expand, UCaaS vendors must apply airtight practices and features that provide real peace of mind for their customers. From a strong commitment to data security to rigorous processes that ensure stringent protection, you’ll need to partner with a vendor whose infrastructure is sound.
Ask for details on the security practices of their platform’s cloud infrastructure, this will let you know whether security is truly in their DNA.
You’ll also want demonstrable details on their data security pledge, the physical security of their environment, data handling and regular security assessments.
Likewise, industry compliance attestations and security certifications will help to illustrate your vendor’s level of commitment to the cause. Look for certifications like the following:
- SOC 2 attestation
- SOC 3 attestation
- ISO 27001 ISO 27017-18 certifications
- STIR/SHAKEN (Spam blocking)
- HITRUST certificate
- HIPAA attestation of compliance
- GDPR
- PCI-certified merchant
- PIPEDA
- C5
2. Data privacy and compliance management
With any UCaaS platform, users can easily share confidential details such as customer information and employee details. Easy collaboration is ultimately one of the most valuable aspects of a UCaaS platform after all. So organisations need to have complete trust in the way their vendor manages compliance and data privacy.
This is where transparency plays a key role. Your chosen vendor’s data privacy policies should be published in a data privacy notice that is publicly available. They must introduce processes that prevent inadvertent or intentional compromise of your protected data and be completely upfront about how data is collated and used.
3. Security and admin controls
Whether it boasts features such as waiting rooms for video calls or multi-factor authentication, it’s worth confirming that your chosen vendor adopts sophisticated capabilities to protect your users and the platform. Advanced controls such as who can enable screen sharing could protect your business from harm. What’s more, your provider should go the extra mile by taking the guesswork out of which controls you might need. Platforms such as RingCentral offer a range of sophisticated security controls, from end-to-end encryption to video host controls and advanced authentication and single sign on (SSO).
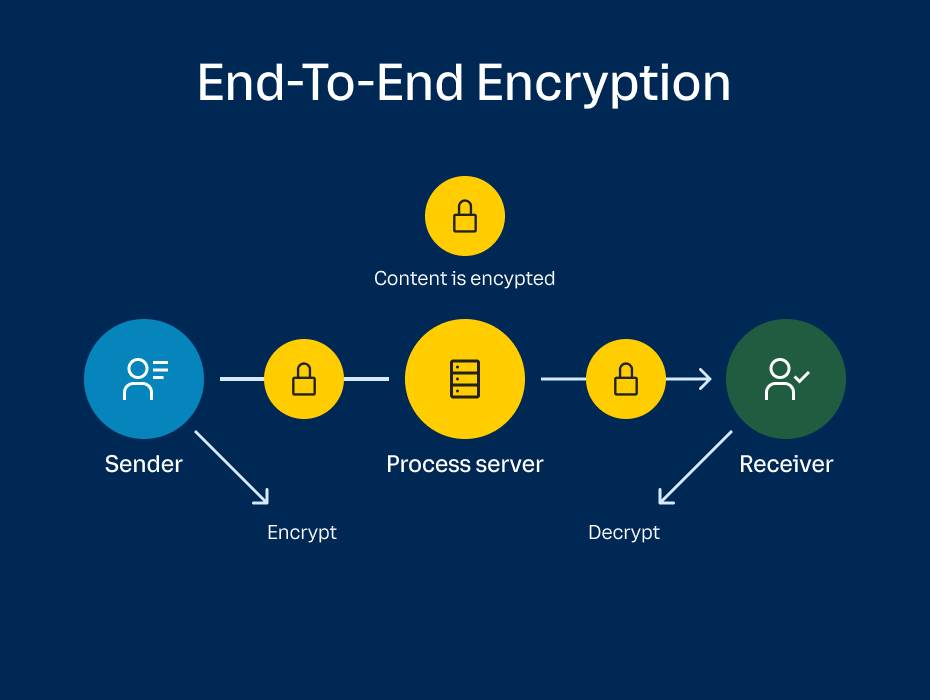
All in all, you’ll want to partner with a UCaaS provider that values the security, privacy and compliance of your data as highly as you do. It’s always going to be worth looking out for these extra details to ensure you get what you need. If you want to discover more about what to look out for, then it’s a good time to read RingCentral’s CISO guide.
Originally published 22 Oct, 2022, updated 14 Nov, 2022